Cybersecurity threats pose a significant challenge in the digital era. Facing increasing threats and evolving attack vectors, a financial services company sought a proactive security strategy to safeguard its assets and maintain customer trust. It adopted a Zero Trust architecture, that implemented network segmentation to isolate critical assets, Identity and Access Management (IAM), continuous monitoring and encryption. By adopting a Zero Trust approach, the organization significantly strengthened its security posture, reducing the risk of data breaches and cyberattacks. Additionally, the implementation of rigorous access controls and encryption measures helped the company achieve compliance with industry regulations and standards.
What is Zero-Trust Framework?
The Zero Trust security framework mandates that all users, whether inside or outside the organization’s network, must undergo authentication, authorization, and continuous validation of security configurations and posture before gaining or maintaining access to applications and data. This approach assumes there is no conventional network perimeter; networks may exist locally, in the cloud, or in a combination or hybrid form, with resources distributed anywhere and employees working from various locations.
Zero Trust serves as a framework for safeguarding infrastructure and data amidst today’s modern digital transformation. It effectively tackles contemporary business challenges, such as securing remote workforce, hybrid cloud setups, and ransomware threats.
How Does Zero Trust Work?
Implementation of Zero Trust integrates technologies like risk-based multi-factor authentication, identity protection, next-generation endpoint security, and robust cloud workload technology. These technologies are used to validate user or system identities, assess access in real-time, and maintain system security. Additionally, Zero Trust necessitates the consideration of data encryption, email security, and verification of asset and endpoint hygiene before connecting to applications.
Contrary to traditional network security, which relied on the “trust but verify” approach, Zero Trust represents a significant shift. In the traditional model, users and endpoints within the organization’s perimeter were automatically trusted, leaving the organization vulnerable to internal malicious actors and legitimate credentials compromised by malicious entities. This outdated model became obsolete with the migration of business operations to the cloud and the widespread adoption of remote work.
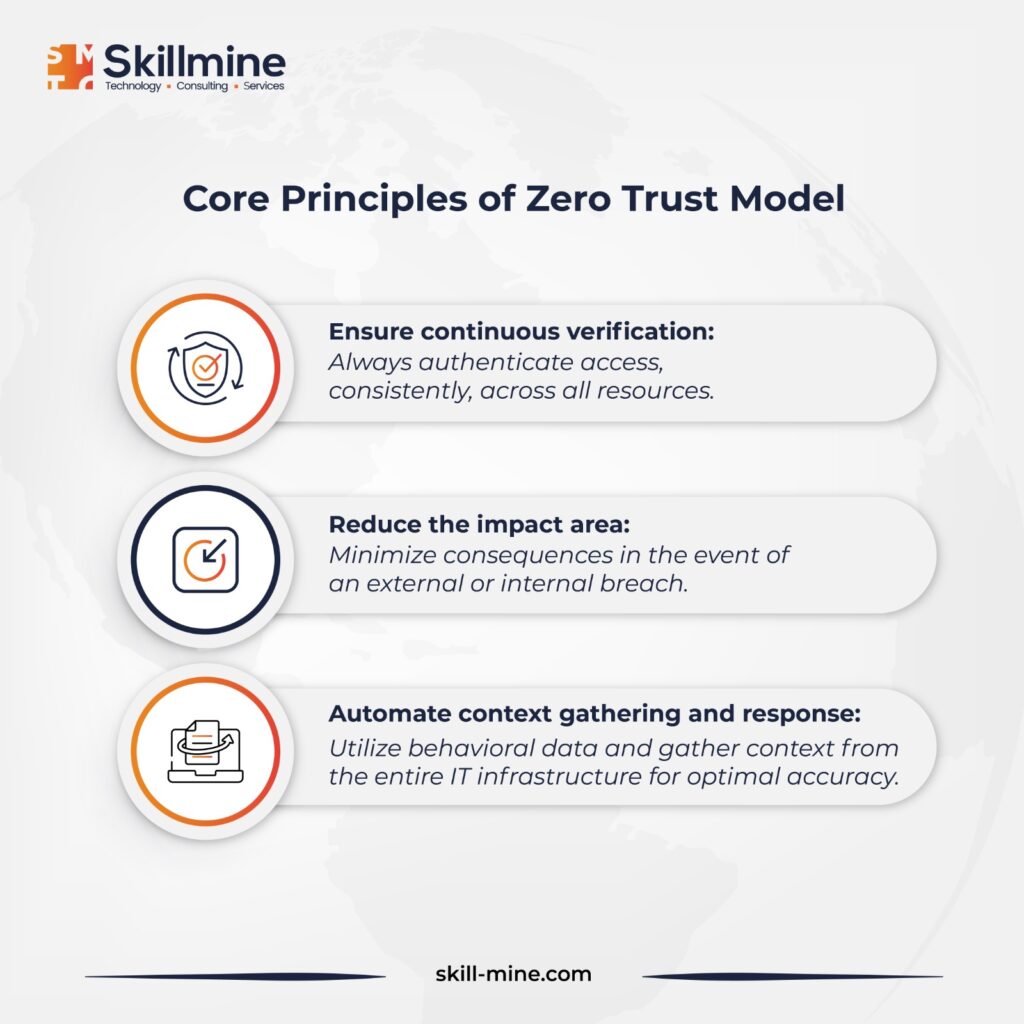
Zero Trust architecture mandates continuous monitoring and validation of user and device privileges and attributes. It also requires policy enforcement based on user and device risk, compliance, and other factors before permitting transactions. Organizations must have full visibility into their service and privileged accounts, establishing controls on their connections and activities. Static validation methods are insufficient as threats and user attributes are dynamic and subject to change.
Therefore, organizations must continuously vet all access requests before granting access to enterprise or cloud assets. Zero Trust policy enforcement relies on real-time visibility into various user and application identity attributes, including user identity and credential type, credential privileges on each device, normal connection patterns, endpoint hardware details, geolocation, firmware versions, authentication risks, operating system versions, installed applications, security incidents, and suspicious activity.
Utilizing analytics tied to extensive enterprise telemetry and threat intelligence enhances algorithmic AI/ML model training for accurate policy responses. Organizations should assess their IT infrastructure and potential attack paths to contain and minimize the impact of breaches, possibly implementing segmentation based on device types, identities, or group functions. For instance, suspicious protocols like RDP or RPC to the domain controller should be scrutinized or restricted to specific credentials.
Popular Zero Trust Frameworks
- Forrester Zero Trust Model: Forrester Research introduced a Zero Trust model that emphasizes the importance of continuous authentication, authorization, and least privilege access controls.
- NIST Zero Trust Architecture: The National Institute of Standards and Technology (NIST) has published guidelines and recommendations for implementing Zero Trust architectures, focusing on the principles of least privilege access, micro-segmentation, and continuous monitoring.
- Google BeyondCorp: BeyondCorp is a Zero Trust security framework developed by Google, emphasizing user and device authentication and access controls based on identity and context rather than network perimeter.
- Microsoft Zero Trust Strategy: Microsoft has developed its Zero Trust strategy, which includes principles such as verifying identities, enforcing least privilege access, and inspecting and logging all network traffic.
- Jericho Forum: The Jericho Forum, now part of The Open Group, has proposed a Zero Trust model called “de-perimeterization,” which advocates for moving away from perimeter-based security to a model based on secure access controls regardless of location or network boundaries.
- Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model (ZTMM): CISA has developed a maturity model to help organizations assess their Zero Trust implementation progress and identify areas for improvement.
Conclusion
Implementing Zero Trust necessitates a comprehensive array of security capabilities and expertise, encompassing identity management, data protection, device and workload security, analytics and monitoring, automation, coordination, and network and endpoint security. Skillmine’s cybersecurity services along with its bespoke solution Auth strengthens Zero Trust by centralizing access management, enhancing security posture and mitigating risks of unauthorized access or breaches.
Looking for expert technology consulting services? Contact us today.





