SECURITY OPERATIONS CENTER

Through our robust, next-gen tools we proactively detect security issues, protect data and systems. We bring comprehensive coverage of the key IT systems and applications into our monitoring scope and respond with standard incident response frameworks.
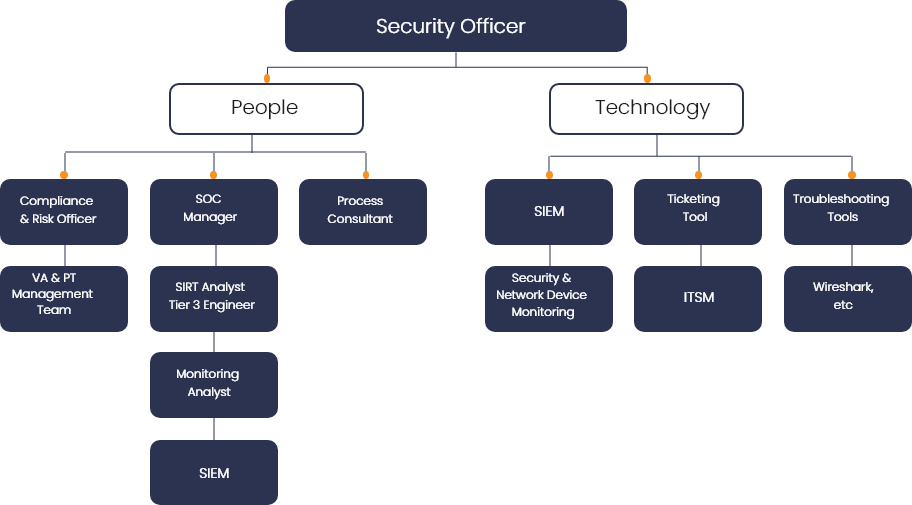
We ensure that people, processes and technology work in tandem to enhance the security posture of the business. Our comprehensive four-part model covers every aspect of security management, leading your SOC program in the right direction.
Incident response, engineering, threat monitoring, and analytics are the four components of the security operations center model. Each of these works closely with the other to ensure that the ongoing process of maintaining security is foolproof.
RISK & COMPLIANCE SERVICES

Transformation & Integration

Penetration
Testing

Managed Security
Services

Strategy, Architecture & Assessment
SECURITY OPERATIONS CENTRE

Network
Security Testing
Vulnerability
Assessments

Risk & Compliance
Assessment

Malicious Code
Analysis
SOC IMPLEMENTATION APPROACH
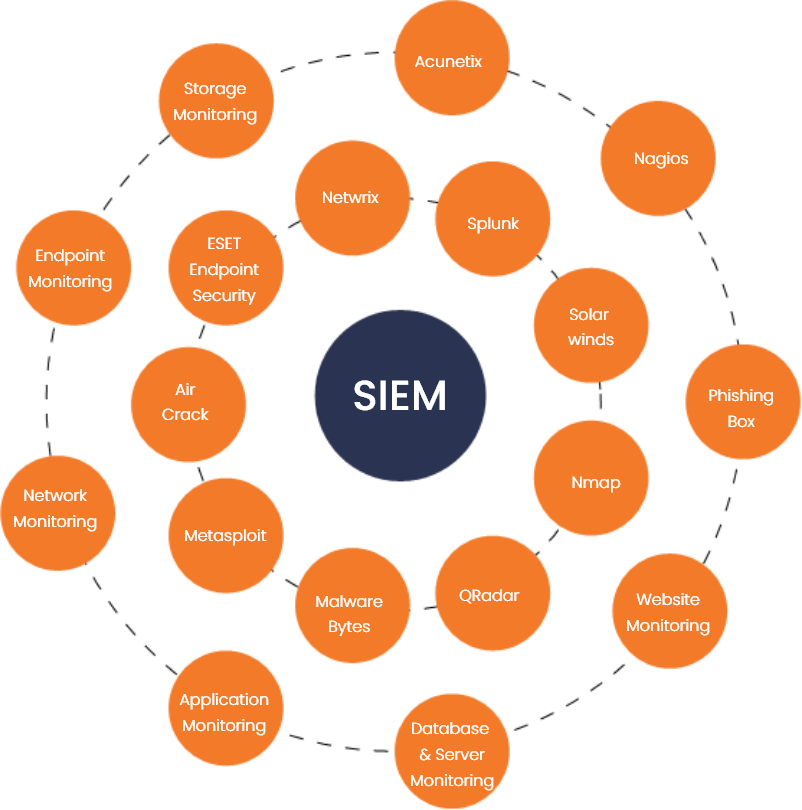
The security operations center services monitors and analyses network, server, endpoint, database, application, website, and other system activities. It keeps an eye out for any unusual activity that could indicate a security event or breach.
The SOC is in charge of properly identifying, analysing, defending, investigating, and reporting potential security events. The SOC’s 24-hour monitoring provides businesses an edge in defending against events and intrusions, regardless of source, time of day, or kind of assault. We ensure that people, processes and technology work in tandem to enhance the security posture of the business. Our comprehensive four-part model covers every aspect of security management, leading your SOC program in the right direction. Incident response, engineering, threat monitoring, and analytics are the four components of the security operations model. Each of these works closely with the other to ensure that the ongoing process of maintaining security is foolproof.
SERVICES MONITORED IN SOC
SOC STRUCTURE
SOC BENEFITS
- Comprehensive coverage with 24/7 monitoring.
- Reduce cybersecurity headcount costs.
- Reduce dwell time & financial impact with robust containment.
- Threat triage, remediation, and incident isolation.
- Security stack insight & compatibility.
- Analytic monitoring & robust response mechanism
- Threat hunting & correlation with events
- Threat intelligence to counter Advanced Persistent Threats (APTs)
- Forensic investigation capabilities
- User and Entity Behaviour Analysis (UEBA)
- Security orchestration, automation and response (SOAR)
- Logging and auditing for compliance
- Cloud-based analytics and operations
- Open architectures and layered analytics
- Implement & integrate DevSecOps
The Security Operation Center (SOC)8uacts as the company’s intelligence hub, collecting data in real-time from the company’s networks, servers, endpoints, and other digital assets and utilizing intelligent automation to identify, prioritize, and respond to potential cybersecurity threats.
The people, processes, and technology that are responsible for monitoring, evaluating, and managing an organization’s information security make up a security operations center.
Most security operations centers have a “hub and spoke” configuration, which allows the company to construct a consolidated data repository that can be used for a variety of purposes. The following are some of the SOC’s activities and responsibilities:
- To provide total visibility into digital activities and better spot irregularities, network monitoring is used.
- Providing techniques for preventing and deflecting a variety of known and unknown threats.
- Threat detection and intelligence capabilities that evaluate the source, impact, and severity of each cyber incident.
- Using a combination of automated technologies and human engagement, decisive incident reaction and remediation is possible.
- Reporting to ensure that all incidents and threats are fed into the data repository in the future, making it more precise and responsive.
- Risk and compliance capabilities to assure compliance with industry and regulatory standards.
In addition to managing specific incidents, the security operations services bring together various data feeds from each asset to build a baseline picture of normal network activity. The SOC then employs this information to detect unusual activity with greater speed and precision.
One of the SOC’s most important features is that it runs constantly, offering monitoring, detection, and response capabilities 24*7. This helps enterprises shorten their “breakout time” — the important window between when an intruder compromises the first machine and when they can move laterally to other sections of the network — by ensuring threats are isolated and handled fast.
Skillmine’s Security Operations Center services involve creating a four-part model that covers all aspects of security management. The four components of Skillmine’s security operations services are incident response, engineering, threat monitoring, and analytics. Each of these groups collaborates closely to guarantee that the ongoing security process remains intact and on schedule. We provide a security operation team with invaluable information to help improve their organization’s security posture.
The improvement of security incident detection through constant monitoring and analysis of data activity is a fundamental benefit of having a security operations center. SOC teams are crucial for ensuring rapid detection and response of security issues by evaluating activity across an organization’s networks, endpoints, servers, and databases around the clock. A SOC’s 24*7 monitoring gives businesses an advantage in defending against incidents and intrusions, regardless of source, time of day, or type of assault.
To achieve good results, the Security Operations Center services must stay current on threat intelligence and use it to strengthen internal detection and defensive processes. The SOC consumes data from within the organization and connects it with information from a variety of external sources to provide insight into risks and vulnerabilities. Newsfeeds, signature updates, incident reports, threat briefs, and vulnerability warnings are all examples of external cyber intelligence that help the SOC stay on top of changing cyber threats. To stay current with threats, SOC members must regularly feed threat intelligence into SOC monitoring systems, and the SOC must have protocols in place to distinguish between true threats and non-threats. Skillmine follows these best practices to generate robust solutions for businesses. Key IT systems and applications are secured by bringing them into our monitoring scope. The security posture of your business is enhanced by formulating a stringent security response framework. We leverage automation to detect and respond to cyber-security threats across the organization in real-time.
Frequently Asked Questions
A security operations center (SOC) is a command center for a team of information technology (IT) professionals with information security (Infosec) expertise who monitor, analyze, and protect an organization from cyber attacks. The SOC continuously monitors internet traffic, networks, desktops, servers, endpoint devices, databases, applications, and other systems for signs of a security incident.
A Security Operations Center’s overarching strategy revolves around threat management, which includes collecting and analyzing suspicious activity data to make the entire organization more secure. Raw data collected by SOC teams is security-relevant and comes from firewalls, threat intelligence, and other sources. Alerts are generated to notify team members immediately if any data is abnormal or shows signs of compromise (IOCs).
One of the most significant advantages of having a Security Operations Center is that it improves security incident detection through continuous monitoring and analysis. The SOC team can analyse networks, servers, and databases through this activity, ensuring the timely detection of security incidents. A SOC can help organizations defend against intrusions at any time, regardless of the type of attack.












