Who would have imagined that insider threats would become the most difficult cybersecurity risks to detect and mitigate especially in high-stakes, data-sensitive industries like BFSI, Pharma, and Healthcare. According to the 2024 Verizon Data Breach Investigations Report (DBIR), insider threats are responsible for over 34% of data breaches globally. This initial access method now accounts for 20% of the data breaches Verizon has observed, a mere two percentage points shy of the leading vector, credential abuse. Phishing ranks third, currently contributing to 16% of data breaches.
Whether driven by malice or error, insider threats can lead to devastating outcomes, including data breaches, regulatory penalties, operational shutdowns, and irreparable reputational damage. As organizations strive to enhance their data breach prevention strategies, integrating behavioral analytics and employee monitoring becomes critical to identifying and mitigating such risks early.
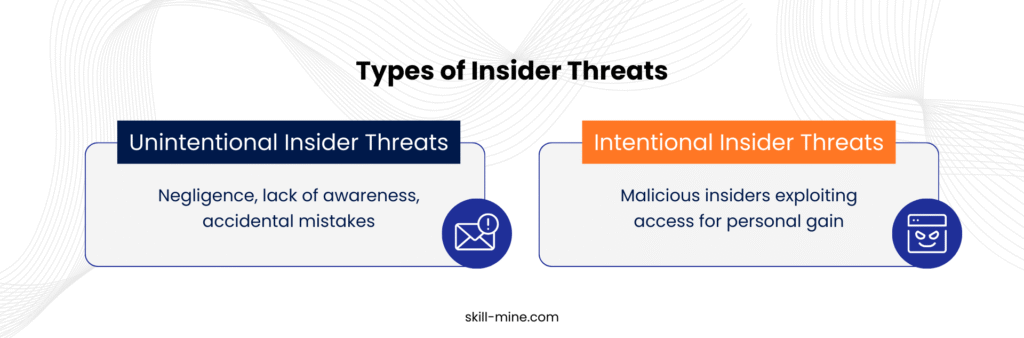
Understanding Insider Threats: Unintentional vs. Intentional
Insider threats typically fall into two categories:
- Unintentional Insider Threats- These arise due to negligence, lack of awareness, or human error. Common scenarios include employees sending sensitive data to the wrong recipients or mishandling login credentials.
- Intentional Insider Threats- These involve malicious activities by individuals who exploit their legitimate access. Such actors may steal intellectual property, manipulate data, or compromise systems for personal gain. According to the Ponemon Institute, it takes an average of 197 days to detect a malicious insider- highlighting the urgent need for advanced monitoring solutions.
User and Entity Behavior Analytics (UEBA): A New Era of Threat Detection
Behavioral analytics, particularly UEBA, is transforming how organizations combat insider threats. By analyzing typical user and entity behavior patterns, UEBA tools detect anomalies such as unusual access times, unauthorized device use, or mass data downloads- that may signal emerging threats.
For example, a global pharmaceutical firm leveraged UEBA to flag a departing employee attempting to transfer proprietary research to an external device. The system detected this unusual behavior two weeks before the employee’s exit, allowing security teams to intervene proactively.
For example, a global pharmaceutical firm leveraged UEBA to flag a departing employee attempting to transfer proprietary research to an external device. The system detected this unusual behavior two weeks before the employee’s exit, allowing security teams to intervene proactively.
Enhancing Security with SIEM and UEBA Integration
While Security Information and Event Management (SIEM) platforms centralize and correlate logs from across an organization’s IT ecosystem, integrating UEBA enhances these systems by adding a behavioral intelligence layer. This combined approach enables:
- Comprehensive Threat Visibility: Monitor user activity and correlate it with system events.
- Faster Detection: Identify abnormal behavior in near real-time.
- Improved Context: Understand the intent behind user actions, not just the actions themselves.
Employee Monitoring and Threat Intelligence
Effective employee monitoring doesn’t mean surveillance—it means strategic oversight. By tracking behavioral risk indicators, organizations can balance privacy with security. When paired with real-time threat intelligence feeds, this approach ensures your cybersecurity posture evolves with the threat landscape.
Automated Playbooks: Respond Faster, Minimize Damage
Automation is crucial in responding to insider threats. Customizable playbooks can trigger immediate actions- such as disabling accounts, alerting administrators, or isolating affected systems—when risky behavior is detected. This reduces response time and limits the scope of potential data breaches.
Building a Resilient Organization
Preventing insider threats goes beyond technology. It requires a holistic approach that includes:
- Security Awareness Training: Organizations that regularly educate employees report a 70% decrease in incidents caused by human error.
- A Security-First Culture: Embedding cybersecurity into daily operations- with visible leadership support- reinforces employee accountability and vigilance.
- Continuous Monitoring and Proactive Threat Hunting: Moving beyond passive detection, proactive threat hunting based on behavioral baselines uncovers subtle risks before they escalate.
Compliance, Risk Reduction, and Skillmine’s Strategic Advantage
Industries subject to stringent data protection regulations such as GDPR, HIPAA, GxP, and PCI DSS must demonstrate ongoing compliance. Skillmine’s UEBA-powered solutions provide:
- Audit-Ready Reports: Automated logs and forensic trails simplify compliance audits and legal investigations.
- Cost Reduction: Organizations with mature insider threat programs spend 23% less on recovery and legal costs post-incident (IBM Cost of Insider Threats Report 2024).
Why Traditional Defenses Are No Longer Enough
Legacy perimeter-based security is ineffective against insider threats, which exploit trusted access and process gaps. Skillmine’s cybersecurity practice bridges this gap by combining:
- Behavior Analytics-driven Security Services
- 24×7
- Vulnerability Assessments and Penetration Testing (VAPT)
- Governance, Risk & Compliance (GRC) Frameworks
Transforming Threat Detection into a Strategic Advantage
In an elevating complex threat landscape, reactive cybersecurity measures fall short. By leveraging behavioral analytics and employee monitoring through UEBA, organizations can proactively identify, mitigate, and neutralize insider threats before they escalate into serious security incidents.
With Skillmine’s expert-driven, automation-enhanced security offerings, enterprises can confidently protect their most valuable assets and drive continuous business enablement- securely and compliantly.
With Skillmine’s expert-driven, automation-enhanced security offerings, enterprises can confidently protect their most valuable assets and drive continuous business enablement- securely and compliantly.





