The financial impact of cyber-physical system (CPS) attacks on businesses is expected to cross $50 billion by 2023, as per a recent Gartner research. It goes on to say that by 2025, 75% of chief executive officers (CEOs) will be personally liable for CPS incidents.
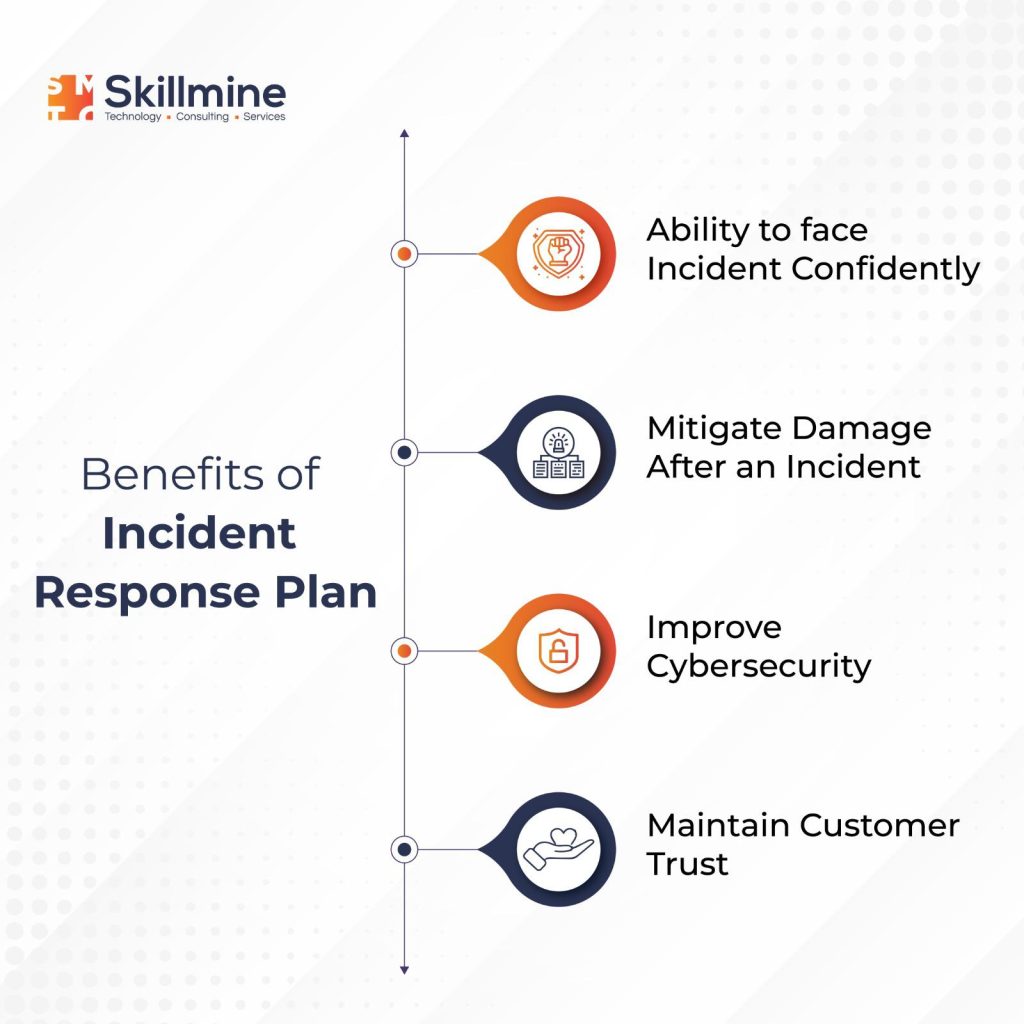
Having a cybersecurity incident response plan (CIRP) is crucial to effectively monitor systems, promptly identify any security incidents, and implement preventive or recovery measures to minimize losses. By having a well-defined incident response plan, your business can quickly respond to potential threats, minimizing the damage caused by cyber attacks and ensuring business continuity.
What is a Cybersecurity Incident Response Plan?
A cybersecurity incident response plan is a comprehensive and documented set of procedures and guidelines that an organization follows in the event of a security breach or cyber attack. The primary objective of a cybersecurity incident response plan is to minimize the damage caused by a cyber attack and restore normal operations as quickly as possible.
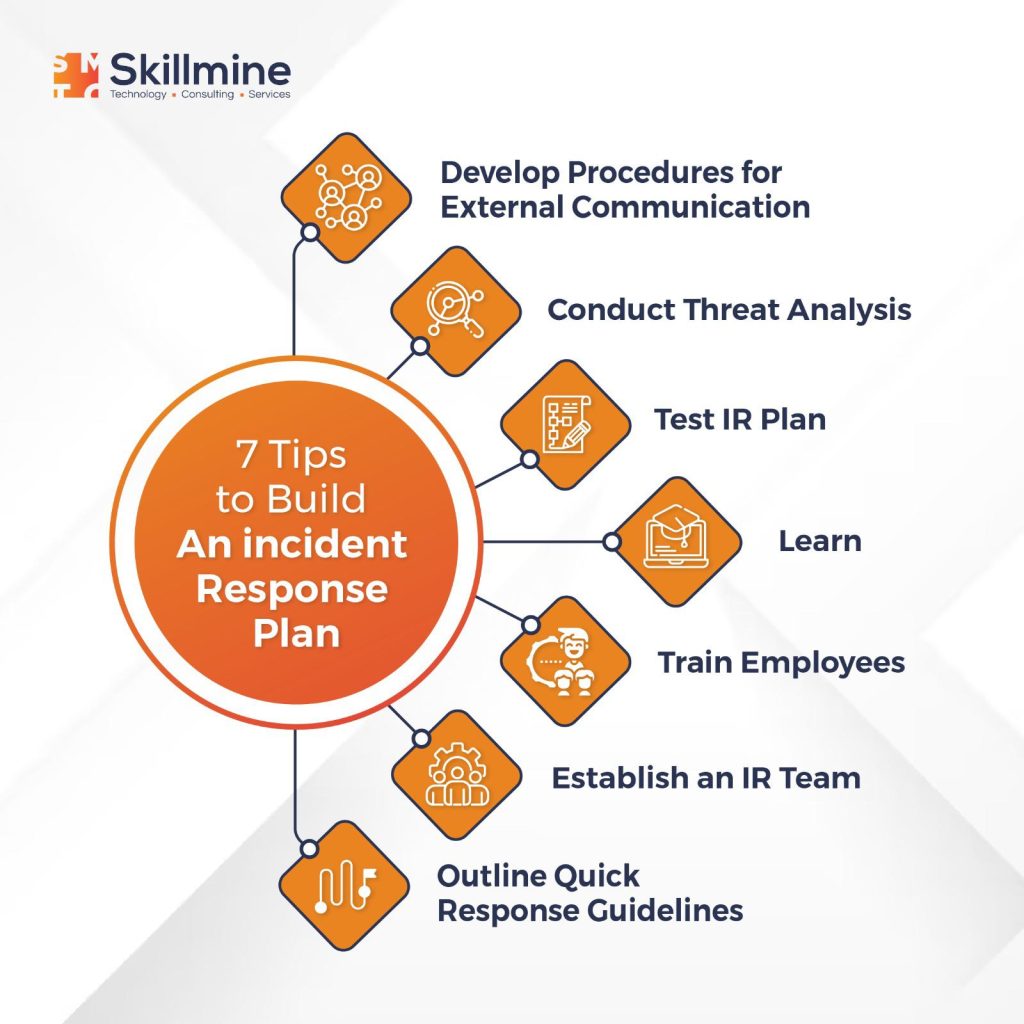
Step-By-Step Guide To Cybersecurity Incident Response
Preparation
The first step in incident response is to be prepared. You should have a detailed incident response plan that includes the following:
- The communication channels.
- The procedures for reporting incidents.
- Identification of the incident response team
- A list of critical assets and data to be protected.
- A detailed recovery plan to restore normal business operations.
- The steps to secure and preserve the affected systems and data.
- A list of authorized and updated contact details of staff members, vendors, and relevant authorities.
Identification
The next step is to identify the incident. You should monitor your systems, networks, and applications for signs of an incident. Common signs of an incident include:
- Unusual network traffic.
- Suspicious emails or files.
- System crashes or freezes
- Changes in system settings.
- Unauthorized access attempts.
Containment
The primary goal of containment is to prevent the incident from spreading further. This may involve shutting down systems or networks, blocking traffic, or isolating affected devices or users.
Analysis
This involves determining the scope and nature of the incident. This analysis may involve forensics, log analysis, and other techniques to determine the source and extent of the incident.
Recovery
This involves restoring the affected systems and data to normal operations. You should also verify that the systems are functioning correctly and have no residual threats.
Lessons Learned
The final step in incident response is to learn from the incident. You should conduct a post-incident review to identify what worked well and what needs improvement. You should also update your incident response plan based on the lessons learned from the incident.
Comparison between businesses with and without a CIRP
S. No. | Business A (Does not have a CIRP) | Business B (Has a CIRP) |
1 | Detects a security incident but not sure how to respond. | Detects a security incident along with its type. |
2 | Takes several hours to prepare a detailed report for declaration. | Quickly declares the incident after confirming with the chief information security officer and incident response experts. |
3 | Since incident identification and declaration took time, the security breach spreads to other business processes besides the initially impacted system. | Immediately isolates the affected system, user, and object from the rest of the business processes. |
4 | No forensic partner to gather evidence for the legal team and advice on recovery. | Calls the forensic partner to gather evidence of the attack and advice on recovery. |
5 | Recovery can’t happen due to a lack of evidence, resulting in a loss. | Timely recovery saves the business from loss.
|
Conclusion
Establishing a Cybersecurity Incident Response Plan (CIRP) can significantly boost your organization’s incident response capability by enabling your security team to proactively and uniformly respond to incidents. With the right resources, tools, and plan of action, your team can confidently navigate the complex incident response process.
Read about the reasons behind Cybersecurity Incidents in Skillmine’s recent blog: Cybersecurity Incidents: What are the real reasons. Interested to do a deep dive into cyberattacks? Watch Skillmine’s Cybersecurity Expert, Anupam Joshi, discuss common cyberattacks in this video session
Looking for expert technology consulting services? Contact us today.