A report by Grand View Research published in February 2021 says that the global Identity and Access Management (IAM) market size was valued at USD 12.2 billion in 2020 and is expected to expand at a compound annual growth rate (CAGR) of 13.7% from 2021 to 2028. The report attributes the growth of the IAM market to factors such as increasing security concerns, the growing adoption of cloud-based IAM solutions, and the rising trend of Bring Your Own Device (BYOD) policies in organizations.
Identity and Access Management (IAM) has become an essential element of security plans for many organizations. Let’s understand more about it.
Importance of IAM
IAM allows companies to manage user access across multiple applications and systems efficiently, streamlining user onboarding and offboarding processes. By implementing IAM solutions, businesses can reduce the risk of insider threats, such as data breaches or intellectual property theft. It is a critical component of an organization’s security posture, providing a layer of protection to ensure that the right people have access to the right information at the right time.
IAM Best Practices
Adopt a Zero Trust Approach to Security
The Zero Trust security model is built upon several core principles, including the concepts of never trusting and always verifying, assuming breach, and applying for least-privileged access. By implementing a Zero Trust model in conjunction with IAM services, organizations can ensure that only authenticated users are granted access to company resources. By enforcing the principle of least-privileged access, access policies are defined, and the authentication process is streamlined, allowing users to access the resources they need without any interruption to their workflows. With the combined power of a Zero Trust strategy and IAM tools, companies can ensure that their resources remain secure and that only authorized personnel can access them.
Enforce a Strong Password Policy
The strength of your IAM technologies is heavily dependent on the identity management best practices and policies that underpin them. When utilizing single sign-on (SSO) tools, it’s essential to ensure that each user’s password is strong, unique, and difficult to guess to adhere to best practices for password and IAM security. To maintain robust password security, passwords should be complex enough to deter cyberattacks, regularly changed, and not used for multiple sign-on requirements.
Organizations should establish an audit schedule to regularly assess user password strength and enforce periodic password changes to further protect resources. By continuously evaluating and improving password policies, companies can bolster their IAM security and reduce the risk of unauthorized access to their resources.
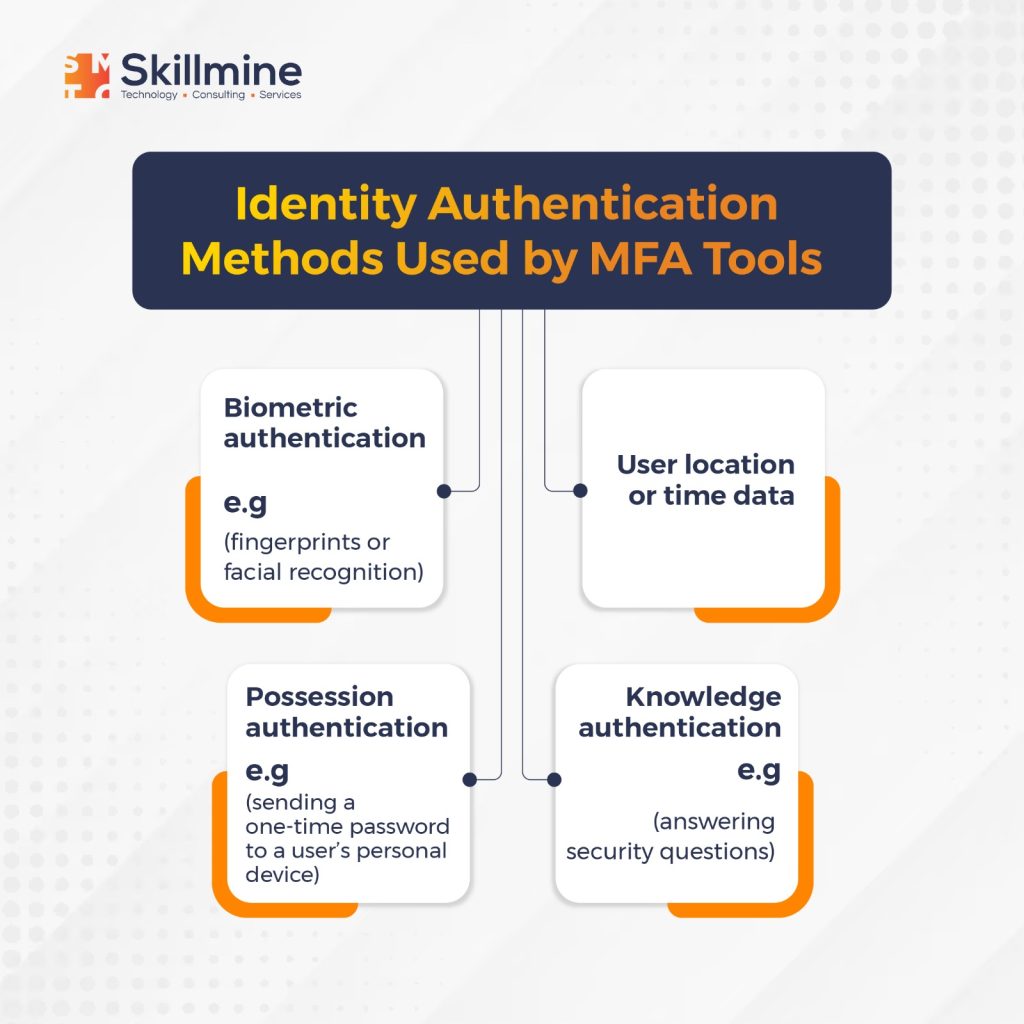
Use Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a critical component of effective identity and access management practices. Without proper user authentication, an organization’s data may be at risk, and unauthorized users may gain access to sensitive information. MFA tools are designed to simplify and automate the authentication process by requiring two or more forms of validation to confirm a user’s identity. By requiring additional forms of identification, such as a fingerprint scan or a code generated by a mobile app, MFA tools can significantly reduce the risk of unauthorized access to company resources.
4 Benefits Skillmine Authenticator can give your business!
- Significantly simplifies your identity management infrastructure.
- Reduces the risk of unauthorized access or escalation of access privileges.
- Preconfigures access controls on new systems, virtual machines (VMs), and containers.
- Reduces the cost of day-to-day operations and the security burden on IT.
Automate Workflows
IAM tools provide IT teams with opportunities to leverage automation to enhance the security of their organization. Automating common tasks like account creation, password changes, and access provisioning or de-provisioning in response to personnel changes can significantly reduce manual errors and streamline workflows. By adopting IAM automation, organizations can ensure compliance with governance needs while also reducing the potential for insider threats when employees leave the organization.
Automated access control helps maintain the security of company resources by quickly revoking access to employees who no longer require it while also simplifying the onboarding process for new employees or those transitioning to a new role. This not only ensures that employees have access to the resources they need but also minimizes the risk of unauthorized access, strengthening the organization’s overall security posture.
Leverage Both Role-Based Access Control and Attribute-Based Access Control Policies
Role-Based Access Control (RBAC) is an access control model that determines access based on a user’s job function or role. This approach ensures that users are granted the minimum privileges necessary to perform their job functions based on their roles, which helps improve security and minimize the risk of data breaches. However, using RBAC alone can become challenging as a company’s tech stack expands and requires more manual provisioning to provide access to additional tools beyond the fundamental access rights.
Attribute-Based Access Control (ABAC) uses policies to define access based on filters and attributes assigned to users. This approach is particularly useful when different departments within an organization require different levels of access. With RBAC and ABAC working in conjunction, organizations can strike a balance between simplicity and granularity in access control, enhancing security while also streamlining workflows.
Conclusion
In conclusion, IAM implementation best practices are essential to ensure that organizations have the appropriate security measures in place to protect their digital assets, maintain compliance, and minimize risks. By adopting these best practices, IT teams can enhance security, streamline workflows, and reduce the potential for errors, ultimately safeguarding their organization against cyber threats.
Our IAM guide can give you valuable information about implementing IAM within your organization. Also check out Authenticator, Skillmine’s homegrown authentication and authorization solution that follows the IAM best practices
Looking for expert technology consulting services? Contact us today.