Table of Contents
In September 2025, India’s CERT-In raised the alarm on a novel malware strain dubbed Shai-Hulud — a name inspired by Dune, a famous science fiction novel, but its behavior is all too real and dangerous.
When India’s CERT-In issues an advisory, it signals a serious security threat that businesses cannot afford to ignore. The latest warning concerns Shai-Hulud, a newly identified malware that is targeting developers and IT ecosystems through the npm open-source package registry.
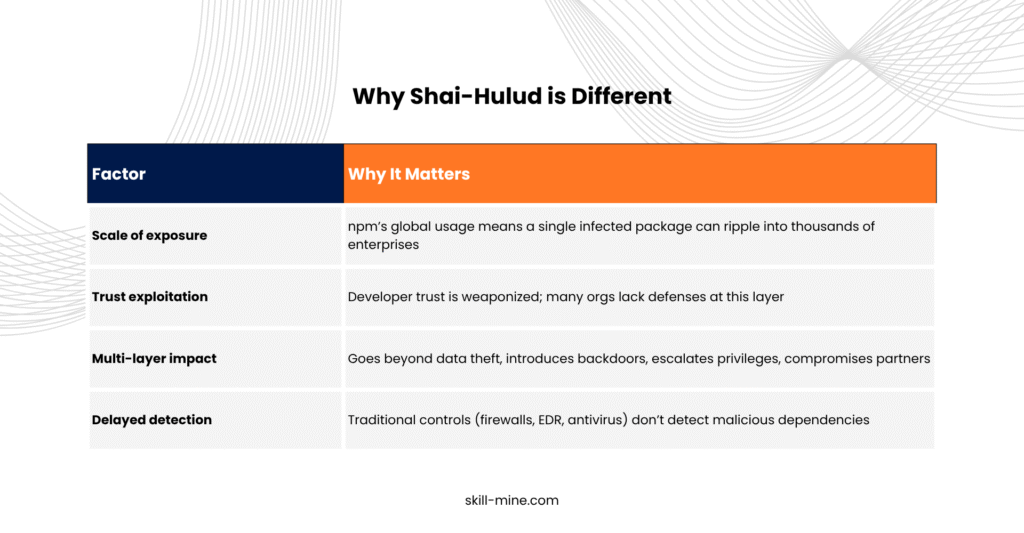
Unlike a typical endpoint exploit and conventional malware strains that attack endpoints or networks directly, Shai-Hulud takes a stealthier, systemic route weaponizing one of the most trusted artifacts in modern development: npm packages. By infiltrating open-source dependencies and leveraging compromised developer accounts, it aims to propagate itself through code supply chains.
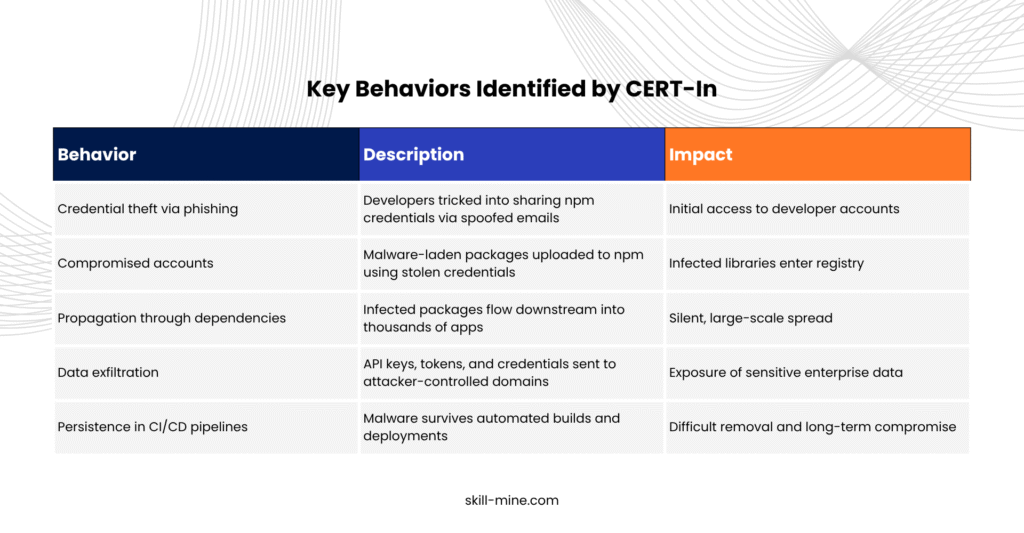
As stated by CERT-In, the malware has already compromised more than 500 npm packages and is propagating across developer networks.
“This attack has the potential to impact start-ups, IT/ITES companies, fintech platforms and e-Governance applications that rely on npm-based software resulting in exposure of credentials, unauthorised code execution and further supply chain compromise,” CERT-In cautioned.
When India’s CERT-In issues an advisory, it signals a serious security threat that businesses cannot afford to ignore. The latest warning concerns Shai-Hulud, a newly identified malware that is targeting developers and IT ecosystems through the npm open-source package registry.
Unlike a typical endpoint exploit and conventional malware strains that attack endpoints or networks directly, Shai-Hulud takes a stealthier, systemic route weaponizing one of the most trusted artifacts in modern development: npm packages. By infiltrating open-source dependencies and leveraging compromised developer accounts, it aims to propagate itself through code supply chains.
As stated by CERT-In, the malware has already compromised more than 500 npm packages and is propagating across developer networks.
“This attack has the potential to impact start-ups, IT/ITES companies, fintech platforms and e-Governance applications that rely on npm-based software resulting in exposure of credentials, unauthorised code execution and further supply chain compromise,” CERT-In cautioned.
What is Shai-Hulud?
Shai-Hulud is a supply chain malware that spreads through npm packages. It has been linked to the compromise of over 500 packages already. The attackers behind it exploit trusted channels — targeting developer accounts, publishing malicious versions of packages, and ensuring these tainted libraries flow downstream into enterprise applications.
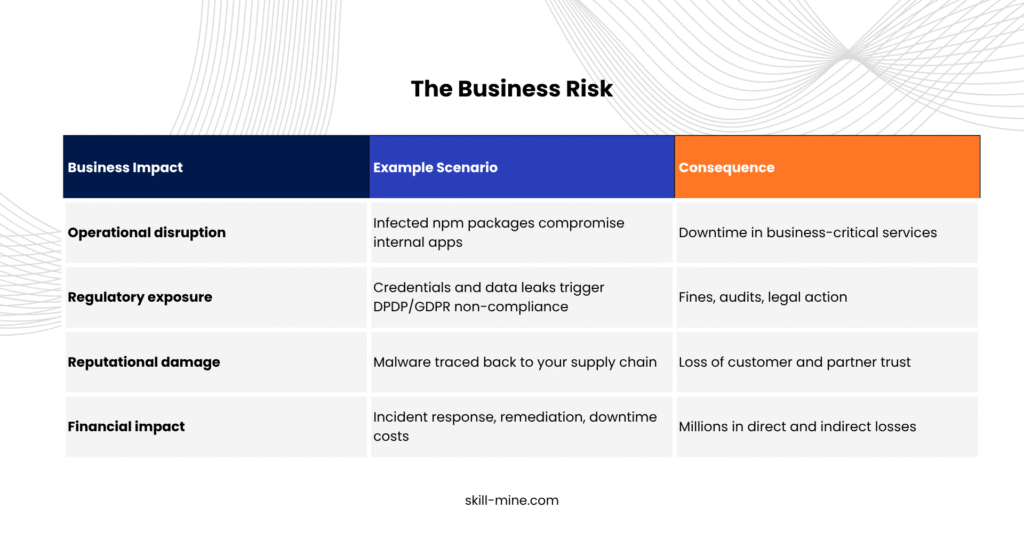
The Business Risk
For leadership teams, Shai-Hulud presents not just a technical issue but an enterprise-wide risk:
The Rising Demand for Cybersecurity Experts
CERT-In has issued specific guidance that every organization should act upon immediately:
Supply chain attacks are evolving fast. Stay informed, stay prepared.
- Enforce phishing-resistant MFA for npm and GitHub accounts.
- Audit dependencies regularly to detect unexpected or malicious packages.
- Rotate all sensitive tokens and credentials that may have been exposed.
- Harden CI/CD pipelines by limiting external scripts, restricting GitHub apps, and enforcing signed commits.
- Monitor for suspicious network calls, especially to domains like webhook[.]site flagged by researchers.
- Train developers and DevOps teams on phishing and supply chain attack patterns.
- Embedding security early in development workflows, from package vetting to CI/CD monitoring.
- Automating dependency scanning and anomaly detection to ensure continuous vigilance.
- Preparing incident playbooks designed for supply chain compromise.
- Elevating supply chain security to board-level governance with regular risk reviews.
- Building resilience through culture and process, making security a first-class citizen in development.
Supply chain attacks are evolving fast. Stay informed, stay prepared.





