For years, vulnerability scanning has been the foundation of enterprise security programs. Scan assets, list CVEs, assign severity scores, patch what you can. This model worked when environments were smaller and attack paths were predictable.
Today, enterprise risk looks very different.
Modern breaches rarely succeed because a vulnerability existed. They succeed because the right vulnerability existed in the right context at the right time. That distinction is exactly where scanning-only approaches fall short.
Today, enterprise risk looks very different.
Modern breaches rarely succeed because a vulnerability existed. They succeed because the right vulnerability existed in the right context at the right time. That distinction is exactly where scanning-only approaches fall short.
The CVE Volume Trap
Traditional scanners prioritise risk based on CVEs and CVSS scores. While this provides structure, it lacks business and operational context.
A critical CVE on an isolated system may pose minimal risk. Meanwhile, a medium-severity flaw on an internet-facing authentication service could be the fastest path to compromise. Without context, security teams end up chasing volume instead of impact.
Industry reports show that enterprises typically remediate less than 15 percent of discovered vulnerabilities each month. The backlog grows, dashboards turn red, and teams feel busy but not safer.
When everything is urgent, clarity disappears.
A critical CVE on an isolated system may pose minimal risk. Meanwhile, a medium-severity flaw on an internet-facing authentication service could be the fastest path to compromise. Without context, security teams end up chasing volume instead of impact.
Industry reports show that enterprises typically remediate less than 15 percent of discovered vulnerabilities each month. The backlog grows, dashboards turn red, and teams feel busy but not safer.
When everything is urgent, clarity disappears.
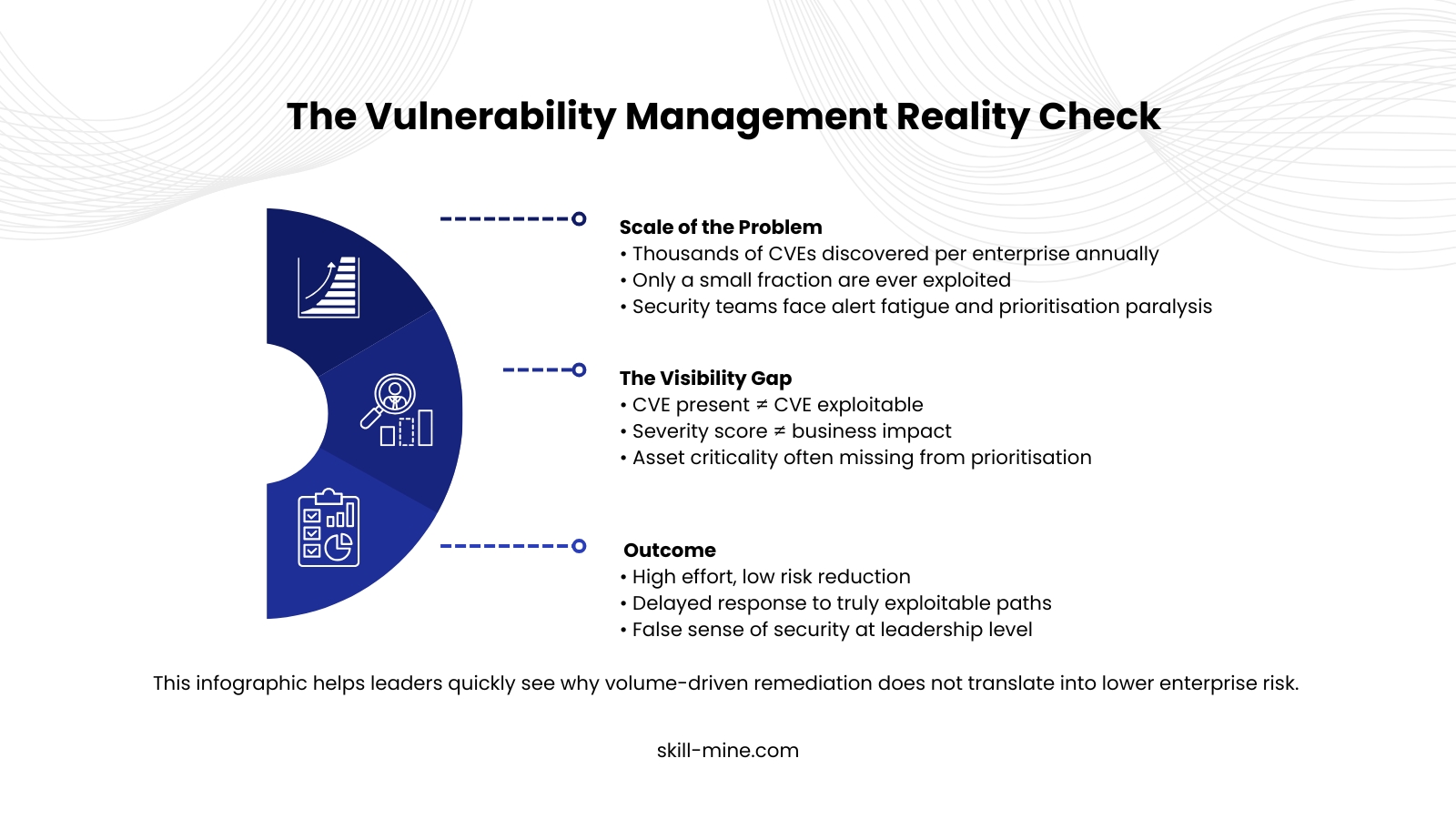
Exploitability Is the Missing Link
Another major limitation of scanning alone is the exploitability gap.
Most scanners identify theoretical weaknesses, not practical attack paths. They do not evaluate whether a vulnerability is actively weaponised, exposed to attackers, or connected to privileged access.
Research consistently shows that fewer than 5 percent of vulnerabilities are exploited in the wild. Yet security teams often treat all high-severity findings as equally dangerous. This leads to wasted cycles and missed signals.
Attackers do not care about scan scores. They care about access, identity, and reach.
Most scanners identify theoretical weaknesses, not practical attack paths. They do not evaluate whether a vulnerability is actively weaponised, exposed to attackers, or connected to privileged access.
Research consistently shows that fewer than 5 percent of vulnerabilities are exploited in the wild. Yet security teams often treat all high-severity findings as equally dangerous. This leads to wasted cycles and missed signals.
Attackers do not care about scan scores. They care about access, identity, and reach.
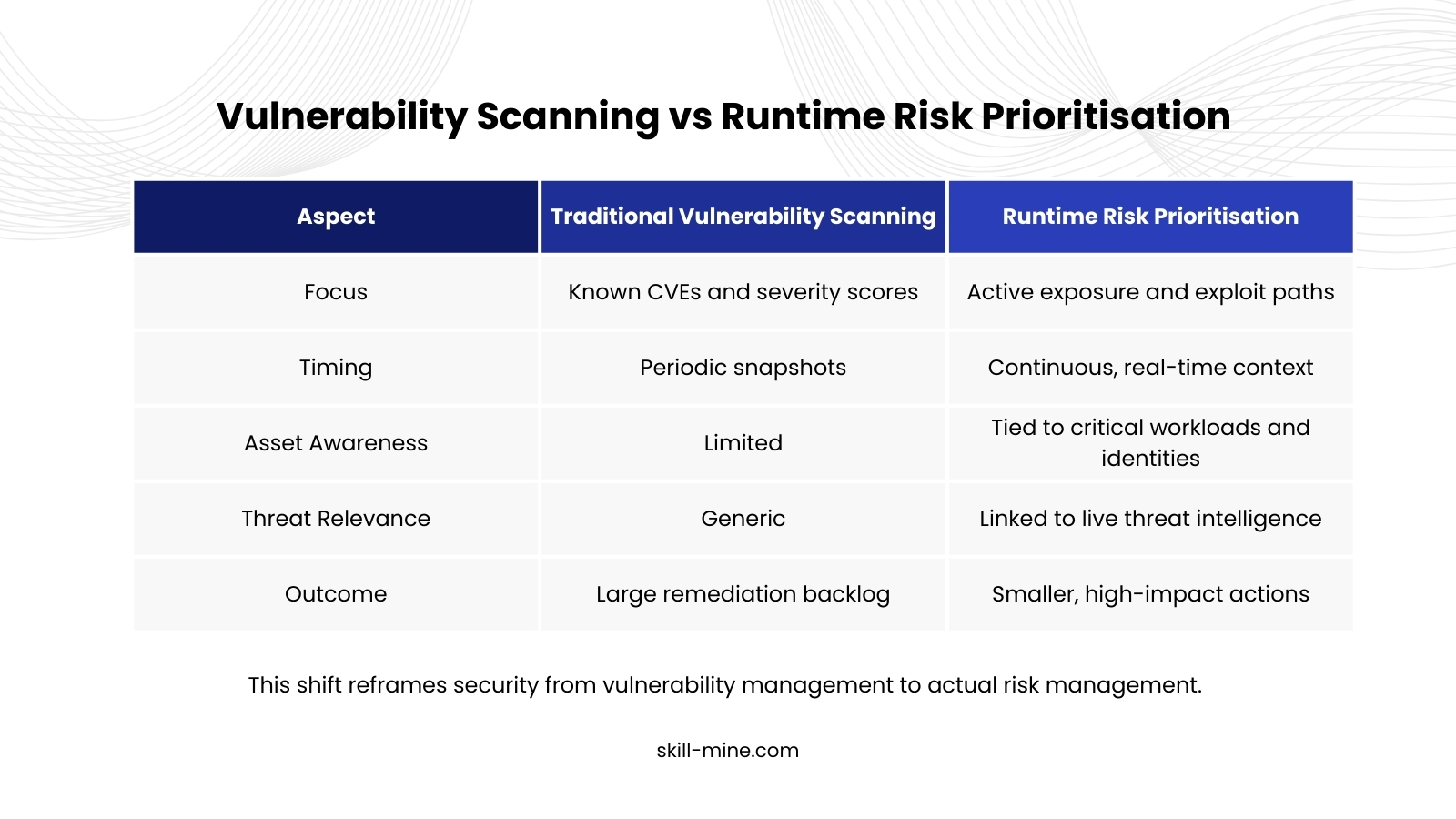
Where Breaches Actually Begin
Modern attacks exploit runtime conditions. Misconfigured permissions, weak authentication flows, exposed services, and identity misuse create opportunities that static scans cannot capture.
Runtime risk prioritisation adds the missing context by correlating vulnerabilities with live workloads, user behavior, network exposure, and threat activity. It answers the questions security leaders actually care about: what can be exploited now and what would hurt the business most.
Runtime risk prioritisation adds the missing context by correlating vulnerabilities with live workloads, user behavior, network exposure, and threat activity. It answers the questions security leaders actually care about: what can be exploited now and what would hurt the business most.
A More Practical Path Forward
Vulnerability scanning remains necessary, but it should be treated as an input, not the end state. Enterprises that reduce risk effectively combine scanning with context, exploitability intelligence, and runtime visibility.
At Skillmine, we help organisations connect vulnerability data with enterprise architecture, operational workflows, and real-world exposure. The focus is on enabling better prioritisation and faster decisions rather than generating more alerts.
Because in today’s threat landscape, risk is not defined by how much you find, but by how clearly you understand what truly matters.
At Skillmine, we help organisations connect vulnerability data with enterprise architecture, operational workflows, and real-world exposure. The focus is on enabling better prioritisation and faster decisions rather than generating more alerts.
Because in today’s threat landscape, risk is not defined by how much you find, but by how clearly you understand what truly matters.





