MFA was supposed to be the silver bullet requiring a second factor like a mobile notification or biometrics to ensure that only the right person is logging into an account. But what happens when attackers don’t need to break the system? Instead, they break the user. In sectors like BFSI and Tech Services, where access to financial data, customer PII, or privileged infrastructure is involved, MFA is standard practice. Yet ironically, it’s being exploited via social engineering, not bypassed by technical force.
What is MFA Fatigue?
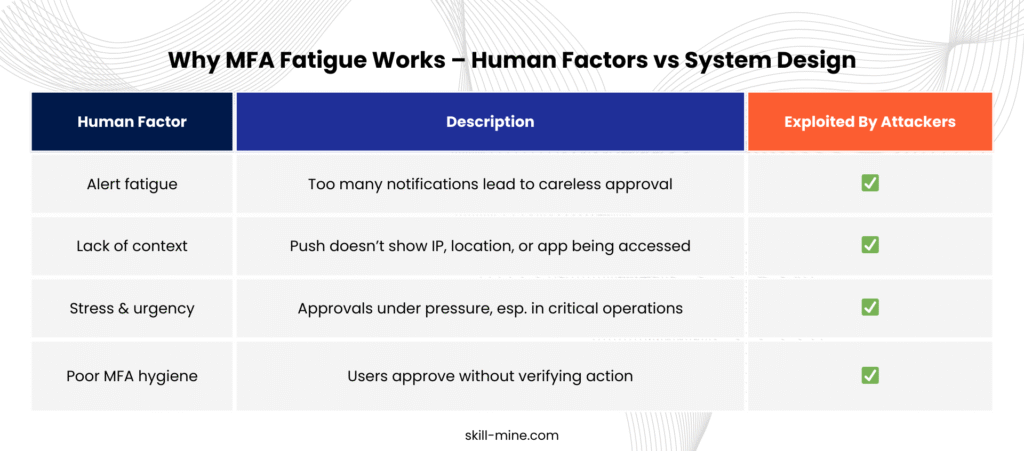
MFA fatigue, also known as MFA bombing, is a technique where attackers repeatedly trigger MFA push notifications on a user’s device in hopes that the user will approve one out of annoyance, confusion, or mistake. This technique doesn’t break MFA, it bypasses it through persistent psychological pressure.
It often begins with stolen login credentials, obtained through phishing, dark web marketplaces, or previous data breaches. Once the attacker attempts to log in, the legitimate user receives a barrage of push-based authentication requests. Eventually, some users, especially under pressure or in high-stress environments, will approve these requests just to stop the interruption.
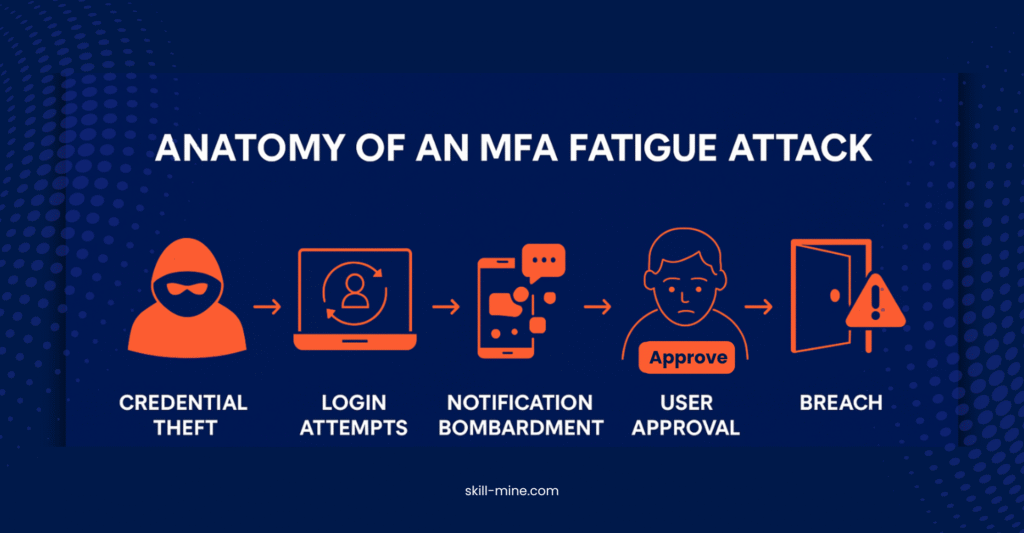
Typical Attack Flow
It often begins with stolen login credentials, obtained through phishing, dark web marketplaces, or previous data breaches. Once the attacker attempts to log in, the legitimate user receives a barrage of push-based authentication requests. Eventually, some users, especially under pressure or in high-stress environments, will approve these requests just to stop the interruption.
Typical Attack Flow
How AI is Reshaping Cyber Defence Strategies?
Credential Theft → Login Attempts → Notification Bombardment → User Approval → Breach
- Attacker steals username/password via phishing/dark web.
- Attacker logs in multiple times, triggering push notifications.
- Victim gets overwhelmed by repeated prompts.
- Victim finally approves one—giving access to the attacker.
How it works?
The attacker has stolen your login credentials, maybe through phishing or a previous data breach. Now, they don’t need to work their way through layers of encryption or firewalls. All they need to do is flood you with repeated push notifications until, under pressure, you approve one out of frustration, distraction, or the need to just get back to work. You think it’s a mistake, but by then, the attacker has gained access.
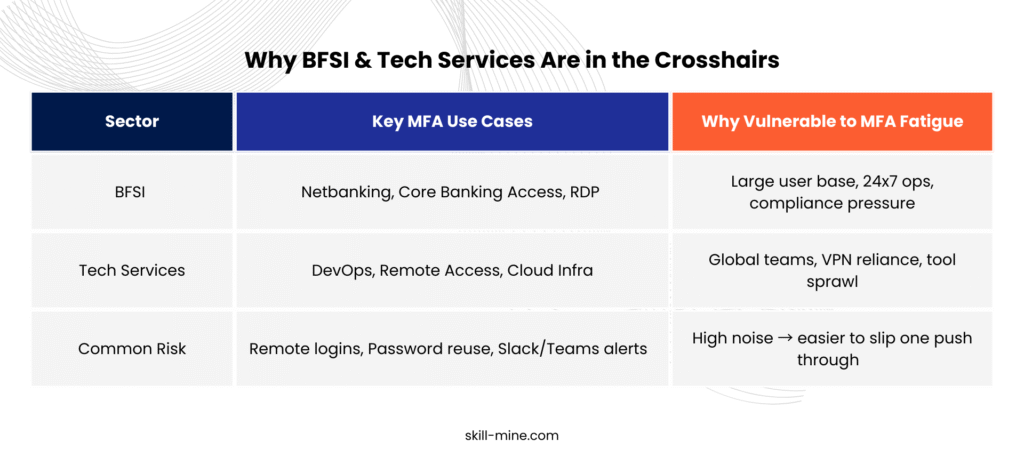
These industries are prime targets because:
- They use MFA widely (for VPNs, banking apps, cloud tools, etc.)
- Their teams work around the clock.
- Employees often approve dozens of prompts a week — from many different tools.
CISA Advisory & Regulatory Recommendations
The Cybersecurity and Infrastructure Security Agency (CISA) has issued comprehensive guidelines to address MFA fatigue and enhance security measures against this evolving threat.
The Cybersecurity and Infrastructure Security Agency (CISA) has issued comprehensive guidelines to address MFA fatigue and enhance security measures against this evolving threat.
CISA’s Key Recommendations:
- Adopt Phishing-Resistant MFA: CISA recommends implementing phishing-resistant MFA, such as FIDO2 security keys or PKI-based smartcards, to block attackers from bypassing MFA through social engineering.
- Implement Number Matching: To reduce accidental approvals, CISA advocates using number matching in MFA applications. This requires users to verify a specific number shown on the screen before approving a request.
- Monitor Denied MFA Requests: Frequent denials of MFA requests can signal a potential compromise. CISA advises organizations to monitor these denials as a proactive measure to spot suspicious activity early.
- Strengthen Contextual MFA: Adding contextual information—like IP addresses, device types, and accessed applications—to MFA prompts helps users verify the legitimacy of requests before approval.
Preventing MFA Fatigue
- Adaptive Authentication: By using adaptive MFA, you can adjust the level of authentication based on factors such as location, device, and login behavior. This approach helps reduce unnecessary MFA prompts while still maintaining high security standards.
- Behavioral Analytics: With machine learning and AI-driven behavioral analytics, abnormal login patterns can be detected in real-time. Unusual activity, such as accessing systems from a different location or device, can trigger additional verification steps, adding another layer of defense.
- Rate Limiting MFA Requests: Implement rate limiting for MFA prompts to control the frequency of requests. This ensures that attackers cannot flood users with repeated prompts, reducing the chance of fatigue-induced approvals.
- Security Audits & Penetration Testing: Regularly assess your MFA systems through penetration testing and security audits. This proactive approach helps uncover potential vulnerabilities and ensures your MFA setup stays ahead of emerging threats.
- User Education: Educating your employees about MFA fatigue is crucial. Ensure they understand the risks and are trained to carefully evaluate MFA requests, especially in high-pressure or off-hours scenarios.
- Single Sign-On (SSO) Integration: Single Sign-On (SSO) solutions help reduce the number of MFA prompts by centralizing authentication across multiple systems. This enhances user convenience while also lowering the attack surface by reducing the number of MFA requests.
Real-World Case Studies: MFA Fatigue in Action
Several high-profile breaches have shown how MFA fatigue can be successfully exploited:
Several high-profile breaches have shown how MFA fatigue can be successfully exploited:
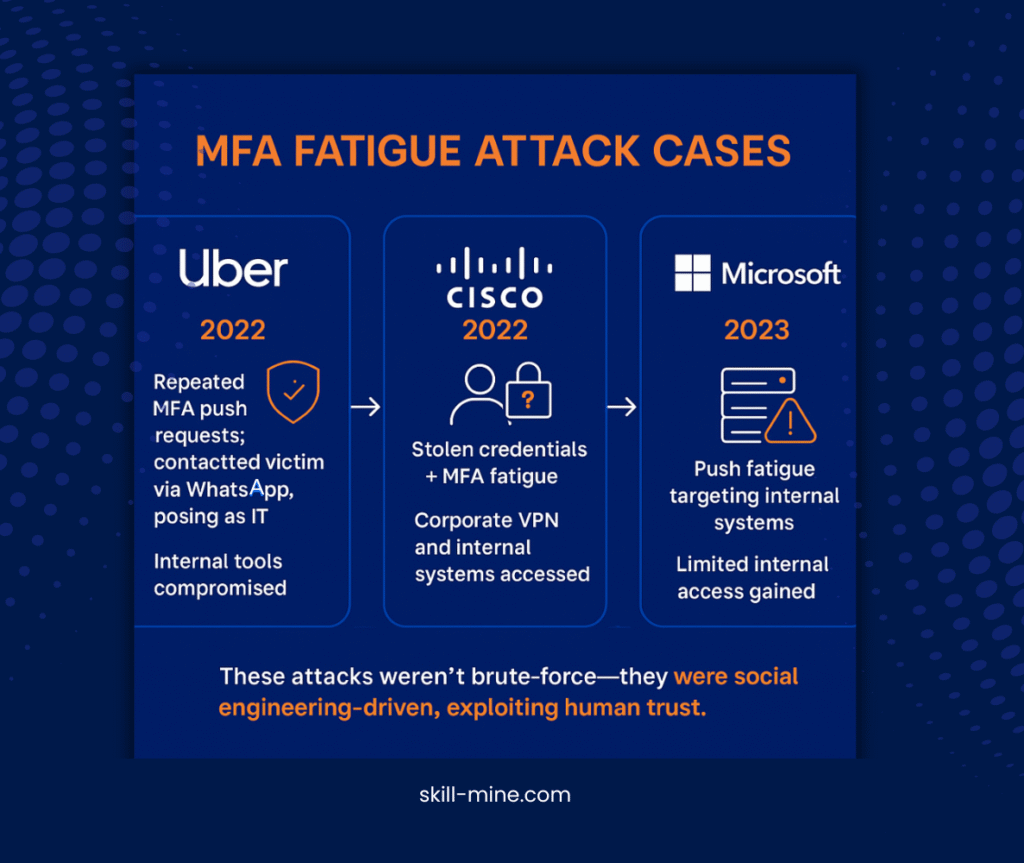
- Uber (2022): Attackers used MFA fatigue alongside social engineering to impersonate IT staff and gain access to Uber’s internal systems. Sensitive data was exposed as a result.
- Cisco (2022): MFA fatigue was leveraged to bypass MFA defenses and access Cisco’s corporate VPN. Despite having strong MFA systems in place, attackers successfully exploited the fatigue factor.
- Microsoft (2023): Internal systems at Microsoft were targeted with MFA fatigue attacks. These incidents showed that even large, sophisticated companies are vulnerable to this type of attack.
Strengthening Your MFA Strategy
As MFA fatigue continues to grow as a risk, it’s crucial to evolve your identity and access management (IAM) strategy. How? Read further
As MFA fatigue continues to grow as a risk, it’s crucial to evolve your identity and access management (IAM) strategy. How? Read further
- Audit Your MFA Setup: Review your MFA strategy to ensure it includes advanced solutions like phishing-resistant authentication, contextual verification, and number matching.
- Real-Time Monitoring: Implement real-time monitoring for any abnormal MFA patterns, and set up alerts to detect potential fatigue-driven attacks early.
- User Vigilance: Create a culture of cybersecurity awareness by regularly training employees to carefully evaluate MFA requests and avoid approving requests under stress or in high-pressure situations.
- Next-Gen Authentication: Consider incorporating biometric authentication, hardware tokens, or adaptive MFA solutions to further reduce the reliance on push notifications, making your system more resistant to fatigue attacks.
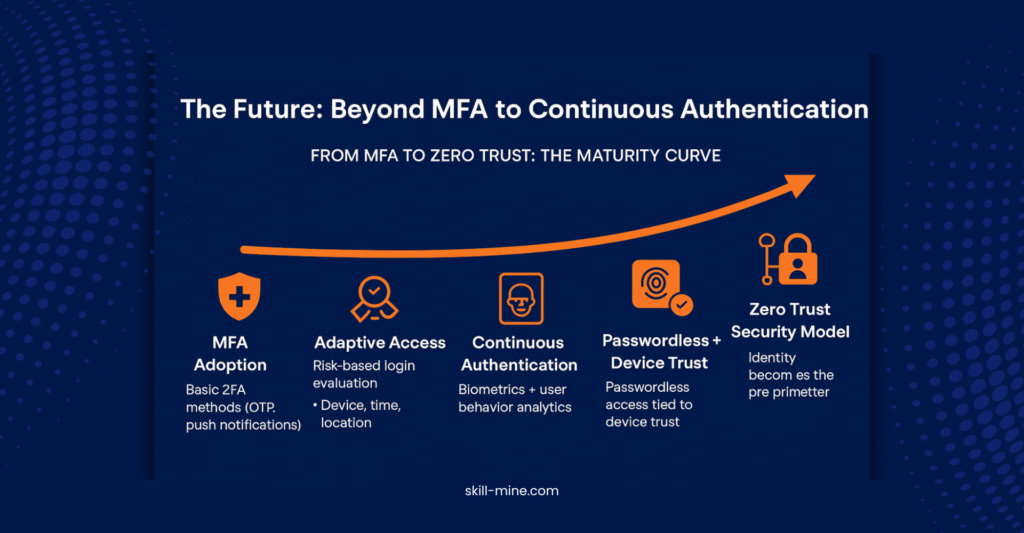
MFA continues to be one of the strongest defenses against unauthorized access, but MFA fatigue represents a critical challenge. The key to staying ahead of the threat lies in continuously evolving your authentication strategies and empowering your teams to recognize and respond to emerging risks. By integrating the right solutions and creating a culture of vigilance, you can ensure that MFA fatigue doesn’t become the opening attackers are waiting for.
If you work in BFSI or Tech Services or any Domain that is critical, now’s the time to:
If you work in BFSI or Tech Services or any Domain that is critical, now’s the time to:
- Revisit your MFA setup
- Look for signs of fatigue-based attacks
- And educate and empower your teams to stay alert
Want to Audit Your MFA Setup?
If you’re wondering whether your MFA strategy is up to date or vulnerable to fatigue-based bypass, let’s talk.
Reach out today to schedule a comprehensive audit of your authentication strategies, and let’s work together to fortify your security. Drop us a message or email on [email protected]. We are ready when you are.





