Alert overload is a crippling issue in which security teams are drowning. The unrelenting stream of notifications, most of which never pose a serious threat, burning out the blue teams while the red teams gain advantage. As the rule of thumb goes, blue teams must be right every time, but red teams only need to be right once.
The Overload Crisis in Modern SOCs
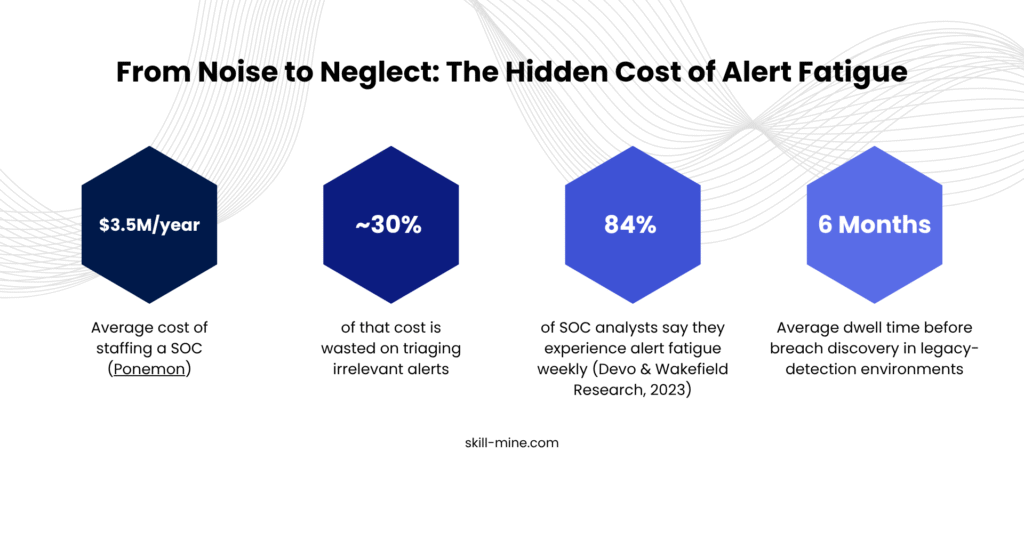
The average enterprise Security Operations Center (SOC) processes over 11,000 alerts per day (Ponemon Institute).
Out of these, 45-80% are false positives or low-fidelity signals (Cydef).
What happens next?
Out of these, 45-80% are false positives or low-fidelity signals (Cydef).
What happens next?
- Analysts waste hours triaging non-issues.
- Critical threats go unnoticed or delayed.
- Burnout rises; retention drops.
- Actual attacks like lateral movement, privilege escalation, and data exfiltration slip through undetected areas.
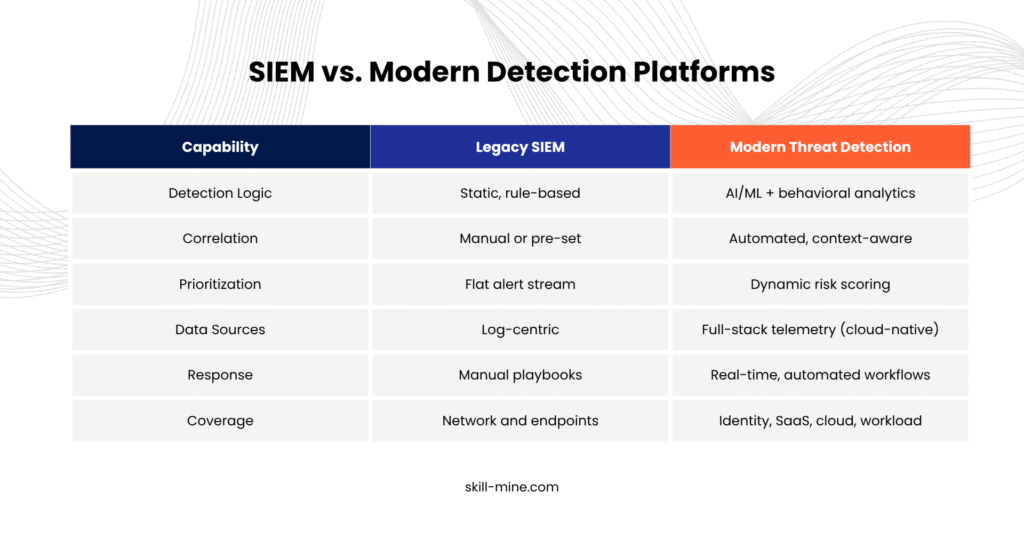
Legacy SIEMs: A 2005 Toolset in a 2025 Threatscape
raditional SIEMs were built for log-heavy, perimeter-based environments. Today’s threats are cloud-native, identity-centric, polymorphic, and operate differently.
With limited scalability and manual processes, here is how the legacy SIEMs fall short:
With limited scalability and manual processes, here is how the legacy SIEMs fall short:
Red Team Tactics: Why Adversaries Are Winning
Red Teams today do not rely on brute force.
They win by blending in and exploiting the very gaps caused by noise and fatigue:
They win by blending in and exploiting the very gaps caused by noise and fatigue:
- Use valid credentials (via phishing or MFA fatigue)
- Move laterally without triggering rules
- Exfiltrate small data chunks below volume thresholds
- Mimic legitimate user behavior Time actions during alert spikes or change windows
The Shift: Toward Intelligence-Led Detection
Modern detection is no longer about logging everything. It is about understanding what matters.
1. Correlation Engines with Context
2. Behavioral Analytics Over Static Rules
Rules catch known threats. Behavioral analytics learns from your environment and flags deviations.
Examples:
3. AI-Powered Threat Scoring & Prioritization
Advanced platforms assign risk scores to each signal using:
“Do not surface every event. Surface what is changing the risk posture.”
1. Correlation Engines with Context
- Unified telemetry from endpoints, firewalls, IAM, network, SaaS, and cloud environments
- Timeline stitching across assets and identities Attack chain reconstruction (MITRE ATT&CK® alignment)
2. Behavioral Analytics Over Static Rules
Rules catch known threats. Behavioral analytics learns from your environment and flags deviations.
Examples:
- Finance user accessing DevOps systems
- Unusual login times from privileged accounts
- Inconsistent IP geo-patterns or devices
- Impossible travel: Multiple logins from distant locations within minutes
3. AI-Powered Threat Scoring & Prioritization
Advanced platforms assign risk scores to each signal using:
- UEBA (User & Entity Behavior Analytics)
- Asset sensitivity profiling Anomaly detection with ML models
- Peer baseline comparison
“Do not surface every event. Surface what is changing the risk posture.”
Automated Response: From Alert to Action Instantly
Detection without a response is delayed. Modern SOCs now implement SOAR (Security Orchestration, Automation, and Response) for real-time containment:
- Quarantine infected endpoint
- Lock compromised account or revoke tokens
- Trigger MFA challenge or session kill
- Open ticket + alert stakeholders
- Launch forensic logging automatically
Blue Team Reality Check
Key Takeaways
Stop drowning in noise. Start defending with clarity.
Want a modern threat detection strategy for your enterprise? Let’s talk. Our experts can assess your current stack and help you transition to an intelligence-led detection model.
- Alert overload is a threat vector, not just an inconvenience.
- Legacy SIEMs struggle with today’s dynamic, identity-aware, multi-stage threats.
- Behavioral detection, AI correlation, and automation are now table stakes.
- Modern SOCs require precision, not volume.
Stop drowning in noise. Start defending with clarity.
Want a modern threat detection strategy for your enterprise? Let’s talk. Our experts can assess your current stack and help you transition to an intelligence-led detection model.





