Cloud-native applications are designed for speed, scale, and constant change. Containers spin up and down, microservices communicate dynamically, and infrastructure is defined in code rather than hardware. While this architecture enables agility, it also introduces a new security reality. One that traditional perimeter-based security models were never designed to handle.
Cloud native security is not about adding more tools. It is about embedding security into how applications are built, deployed, and operated.
Cloud native security is not about adding more tools. It is about embedding security into how applications are built, deployed, and operated.
Why Traditional Security Models Break in the Cloud
Legacy security approaches assume static infrastructure. Fixed servers, known IPs, and clear network boundaries. Cloud-native environments challenge all of this.
Key limitations of traditional models include:
Key limitations of traditional models include:
- Short-lived workloads that outpace manual controls
- East-west traffic between microservices that bypass perimeter defenses
- Infrastructure changes driven by CI/CD pipelines rather than administrators
- Shared responsibility models that blur ownership
What Cloud Native Security Actually Means
Cloud native security focuses on protecting applications across their entire lifecycle. From code to runtime.
It emphasizes:
It emphasizes:
- Secure-by-design architectures
- Continuous security validation
- Identity-based access instead of network trust
- Automation over manual intervention
Core Pillars of Cloud Native Security
At its foundation, cloud native security rests on a few critical principles.
- Shift Left Security: Detect issues early in code, dependencies, and configurations
- Zero Trust: Never assume trust based on location. Verify every request
- Runtime Protection: Monitor the behavior of containers and services in real time
- Policy as Code: Enforce security rules automatically and consistently
- Observability: Maintain visibility across logs, metrics, and traces
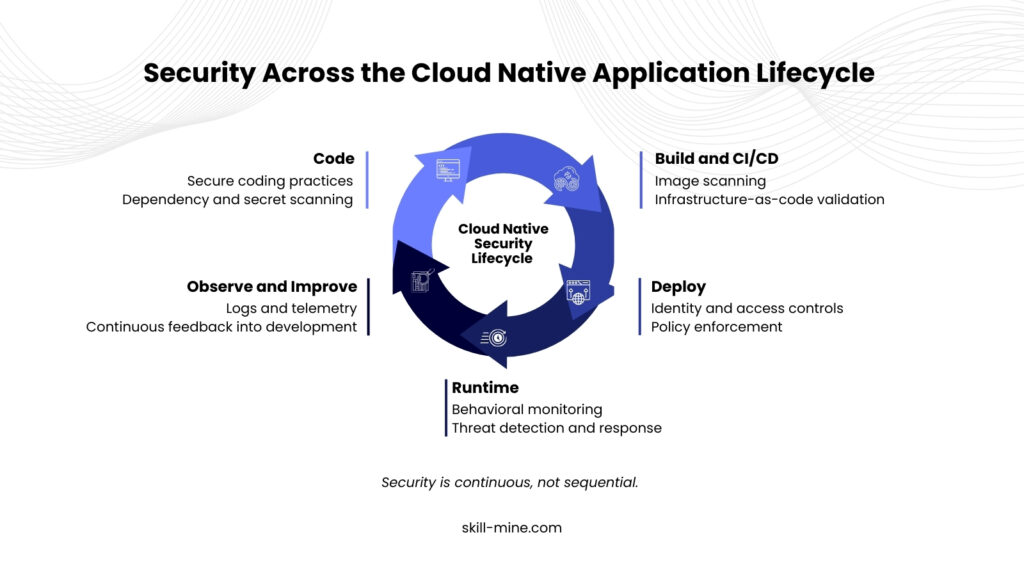
The Role of Automation and Context
In cloud-native environments, scale makes manual security impractical. Automation is essential. However, automation without context can create noise. Effective cloud native security combines automated controls with contextual intelligence. This allows teams to prioritize real risk rather than theoretical exposure.
This balance reduces alert fatigue and improves response times without slowing innovation.
This balance reduces alert fatigue and improves response times without slowing innovation.
Final Thought
Cloud native security is not about locking systems down. It is about enabling teams to move fast while maintaining control. Organizations that adopt this mindset do not treat security as a blocker. They treat it as an architectural capability.
In the cloud, security does not protect the perimeter. It protects the process.
As cloud-native environments grow more complex, security must evolve alongside architecture, pipelines, and operating models.
Skillmine supports organizations in navigating this shift by aligning cloud native security with real-world application design and operational realities. The focus is on building security foundations that scale naturally with modern infrastructure and development practices.
In the cloud, security does not protect the perimeter. It protects the process.
As cloud-native environments grow more complex, security must evolve alongside architecture, pipelines, and operating models.
Skillmine supports organizations in navigating this shift by aligning cloud native security with real-world application design and operational realities. The focus is on building security foundations that scale naturally with modern infrastructure and development practices.





