The global cybersecurity market is projected to hit $266 billion by 2027, according to a 2022 report by Markets and Markets, a market research giant. One recent high-profile cyber-attack was a supply chain attack discovered in December 2020. In a supply chain attack, the less secure elements in the supply chain are targeted to destroy the organization. The attack affected numerous government agencies and businesses that used the third-party software, including the U.S. government.
The attackers, believed to be state-sponsored, inserted malicious code into the software, which is used for network monitoring and management. The code allowed the attackers to access sensitive information, including email communications and government documents. The attack is estimated to have affected as many as 18,000 customers, with at least 250 organizations targeted directly.
How can businesses avoid such cyberattacks? Here are some best practices that companies like yours can follow!
Develop a comprehensive cybersecurity strategy: This includes establishing clear policies, procedures, and guidelines for managing cyber risks. Many computing businesses have successfully implemented comprehensive cybersecurity strategies. Their approach to cybersecurity is guided by Cybersecurity Policy Framework, which outlines principles and practices that aim to protect its networks, data, and customers from cyber threats. Vulnerabilities are addressed through regular software updates, incorporation of Role-Based Access Control (RBAC), setting up of Multi-Factor Authentication (MFA) and implementation of Intrusion Detection Systems (IDS), and spam filters.
Conduct regular risk assessments
Conducting cyber risk assessments offer the following benefits to organisations:
- Systematic identification of current cybersecurity vulnerabilities.
- Reviewing the ability of the company in combating security concerns.
- Development of a practical, step-by-step manual for enhancing the company’s security system and avoiding malicious attacks.
Conducting regular penetration testing, tabletop exercises where a cyber-attack is simulated to test incident response procedures, etc accompany the risk assessment process.
Train employees on cybersecurity
Employees are often the weakest link in an organization’s cybersecurity. Ensuring that employees are well-trained on cybersecurity best practices is critical to reducing the risk of a successful cyber-attack. Skillmine offers its customers a wide range of cybersecurity services and prioritises ensuring its employees are well-trained in cybersecurity best practices. Skillmine conducts red teaming to test cyber resilience and provides cybersecurity certifications to encourage a culture of cybersecurity.
Conduct regular audits
A cybersecurity (Types of Cyber security) audit is an examination of your company’s information technology infrastructure. The audit detects high-risk practises, threats, and vulnerabilities. It is a technique used to assess how well your business complies with security standards. An audit verifies the efficiency of the policies and procedures. Regular audits help ensure that cybersecurity policies and procedures are followed and that the organization complies with relevant regulations and standards. According to ISACA, an international association focusing on IT governance, here are some vulnerabilities, that an audit help in tracking.
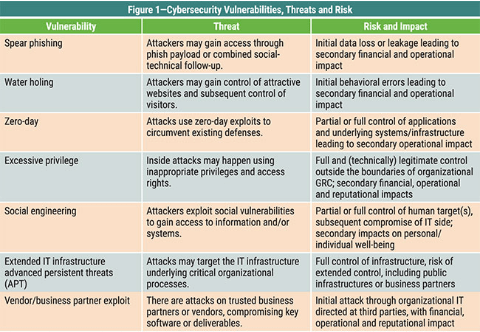
Conclusion
cybersecurity is critical to global governance, risk, and compliance. It is also essential for organizations to establish a culture of cybersecurity that emphasizes the shared responsibility for security across the organization. By implementing these best practices and staying up-to-date on the latest cybersecurity threats and trends, organizations can minimize the risk of cyber-attacks and protect their sensitive data. However, it is crucial to recognize that cybersecurity is an ongoing process that requires continuous monitoring and improvement to stay ahead of evolving threats.
Looking for expert technology consulting services? Contact us today.





