DevOps is a collection of methods and tools that elevate an organization’s capacity to deliver software products, services, enhancements, and upgrades at the velocity of business, employing a distributed agile methodology. Besides reducing the time to market, it allows companies to scale and cater to evolving customer expectations.
The DevOps philosophy seamlessly combines the ‘Development’ and ‘Operational’ teams into a coherent unit, allowing engineers to work across the whole application lifecycle, developing a diverse set of abilities that are not limited to a particular function. The DevOps framework is a sum of:
- DevOps Technologies: It primarily involves the cloud, containerized architectures, serverless deployments, Open-source Libraries that enable people to ‘Assemble’ software rather than the conventional approach to ‘Building’ software.
- DevOps Methodologies: Using Microservices for the benefits of modularity, continuous development, continuous integrations, continuous monitoring, continuous testing, and continuous deployment, changing how people’ Work’.
- DevOps Shared Ownership: A collaborative approach, ensuring that it is everybody’s responsibility to enable the product to meet the necessary quality control benchmarks.
Security: An overarching concern in DevOps
- The security of the application has profound implications and projects a wide range of technological and cultural variables. Nevertheless, security issues in DevOps are frequently emanated from the conflicting aims of the developers and security professionals. Developers strive to get their product through the pipeline as rapidly as possible, while security teams focus on eliminating vulnerabilities, which might stall or delay deployments.
- While delivering at the speed of business, security is often deprioritized, resulting in misconfigurations, unresolved vulnerabilities, and other loopholes, exposing the product to breaches or malfunctions.
- The pervasive cultural aversion to security and testing is a formidable barrier from a development standpoint. The developer’s propensity to fix issues as patches lead to an exponential rise in costs and constitute a significant drag on the DevOps culture.
- DevOps mainly relies on cloud-based infrastructure for the proven benefits. However, operating on immature or open-source technologies may expose the entire lifecycle to vulnerabilities that malicious actors can exploit and monetize.
- Inadequate access controls can be used to exploit software with access tokens and master credentials.
In a recent survey conducted by Gartner, it was concluded that collaboration layered by information security is crucial for successful DevOps outcomes. The study points at a surge in interest among the IT leaders for effectively embedding securities into their DevOps culture. Further, a similar report by Foresters highlights the Best Practices of ‘Static Application Security Testing Usages’ for developers.
What is the way forward in integrating Security DevOps?
The answer is DevSecOps, an approach that seeks to plug Security into DevOps’s continuous delivery modules. Embracing DevSecOps necessitates a shift in mindset across the organization, affecting procedures, people, and the tools they employ, with an unprecedented focus on automation.
Why DevSecOps?
DevSecOps is an institutional and technological paradigm that blends project management workflows with automated IT solutions to create a more secure development and delivery environment. It incorporates operational security audits and testing into agile development and DevOps workflows, ensuring that cybersecurity is incorporated at the product’s development phase rather than an ad hoc attachment post-release.
Reimaging the lifecycle with DevSecOps
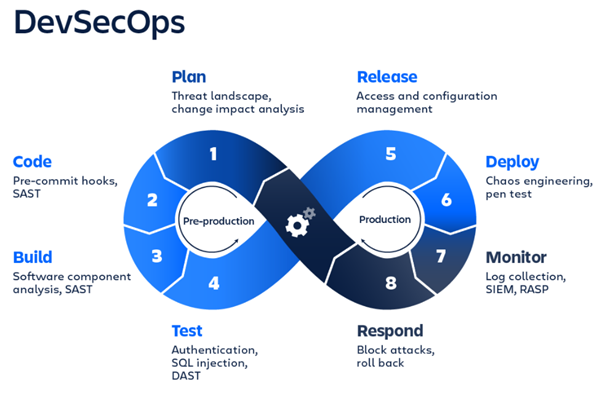
Plan: Before building a product, the teams should invest time and resources in collaboration, discussion, review, and security analysis. The teams should conduct scrums to brainstorm and plan, outlining the ‘where,’ ‘how,’ and ‘when’ of the security testing. IriusRisk, a threat modeling tool, is a popular choice for steering the planning phase. Jira, widely leveraged for the issue and project tracking roles, can drive seamless collaboration and communication between resources during this phase.
Code: Developers can use DevSecOps technologies and quality control processes like Static code analysis, code reviews, and pre-commit hooks to write more secure codes that enforce integrity. The most prominent security code tools are Gerrit, Phabricator, SpotBugs, PMD, CheckStyle, and Find Security Bugs, along with the usage of Git for repository operations and version control.
Build: The build process starts when the developer commits codes and artifacts to the Git repository. Most DevSecOps tools help automate the build process by incorporating it in the CI/CD pipeline. Software component analysis, static application software testing (SAST), and unit tests are essential security approaches. OWASP Dependency-Check, SonarQube, SourceClear, Retire.js, Checkmarx, and Snyk are well-known tools for performing build phase analysis.
Test: The test phase commences when the artifact is built and deployed successfully to staging or testing environments. Building a DevSecOps program for testing puts more focus on dynamic application security testing (DAST) tools. User authentication, authorization, SQL injection, and API-related endpoints are some common flaws tested for security purposes with these tools. BDD Automated Security Tests, JBroFuzz, Arachi, IBM AppScan, Boofuzz, OWASP ZAP, SecApp suite, and GAUNTLET are just a few of the testing tools available that support various coding languages.
Release: After successful completion of the test phases is followed by Release. It examines environment configuration variables such as user access control, secret data management, and network firewall access, ensuring the security of runtime environment architecture. Common followed process consideration is to employ the principle of least privilege (PoLP). Configuration management technologies are essential for security during the release phase. The configuration of the system can then be audited and examined. The goal is to build an immutable design for the product. Adhering to the NIST and Center for Internet Security ensures software robustness. Ansible, Puppet, HashiCorp Terraform, Chef, and Docker are the most central configuration management systems.
Deploy: Itchecks for the configuration variable mismatches between production and lower environments. Production TLS and DRM certificates are also validated and examined for possible discrepancies. Runtime verification technologies like Osquery, Falco, and Tripwire, which gather information from a running system to assess whether it operates as intended, are helpful during the deployment process. Chaos engineering techniques replicating Server crashes, hard disc failures, DDoS attacks, Load running, and interrupted network connections are tested.
Benefits of DevSecOps:
Building a DevSecOps culture focuses on integrating the traditionally separate development, security, and operations functions into a collaborative shared-responsibility model. It brings forth:
- Traceability: In an organization, DevSecOps is critical because it successfully minimizes bugs, ensures code security in application development, and improves code maintainability. It contributes towards delivering superior value and cost leadership.
- Audit: DevSecOps aids in meeting regulatory requirements. To meet compliances, the procedural, technological, and administrative security measures should be well-documented.
- Transparency: DevSecOps manages the entire lifecycle through real-time notifications and engagements. It dramatically enhances situational awareness of the ongoing changes in the environment and possible attempts of cyber intrusions.
Why choose Skillmine?
In an era where security, engineering, and compliance must move in unison to enable the desired outcomes, DevSecOps is an idea whose time has come. It is mission-critical for organizations to create a culture of shared responsibility where the company’s security posture and commitment to its customers are unequivocally acknowledged.
While driving such shifts at scale can be cumbersome for most organizations, trusting a subject matter expert in DevSecOps can resolve the complexities and rapidly bring the desired value. Skillmine is a global leader in IT consulting and managed services that have evolved its offering through over a decade of market exposure and a pervasive presence across five geographies. For our partners, we bring a diverse DevSecOps solutions portfolio. It guarantees the end-objectives through collaborative discovery, Knowledge Management, proven Best Practices, and implementation excellence targeted to reduce the Total Cost of Ownership and maximize value.
Looking for expert technology consulting services? Contact us today.





