Deloitte’s 2023 Global Future of Cyber Survey says that 91% of organizations reported at least one cyber incident—up 3% from the previous year. 56% of respondents reported that they suffered related consequences to a moderate or large extent. On the brighter side, 86% of cyber decision-makers say their focus on cyber has significantly contributed positively to business. Establishing a strong cyber foundation is crucial for prioritizing digital transformation initiatives and ultimately ensuring the success of businesses. API authentication is vital in bolstering cybersecurity by ensuring that only authorized users and systems gain access to sensitive data and functionalities.
What is API Authentication?
API authentication involves verifying the identity of a user initiating an API request and is a fundamental element of API security. Various forms of API authentication exist, including HTTP basic authentication, API key authentication, JWT, and OAuth, each presenting distinct advantages, drawbacks, and ideal scenarios. However, the overarching aim of all API authentication mechanisms remains consistent: safeguarding sensitive data and preventing misuse of the API.
Importance of API Authentication
Numerous business teams have embraced the API-first development paradigm, wherein applications are envisioned and constructed as an amalgamation of services disseminated via APIs. Under this methodology, teams accentuate the importance of API quality and security to uphold their APIs’ high performance and scalability while fortifying defences against potential attackers. API authentication emerges as a pivotal mechanism through which APIs are fortified, empowering teams to shield sensitive data, foster user trust, and uphold the integrity of the organization’s brand.
How Does API Authentication Work?
The dynamics of API authentication vary depending on the chosen method. One common approach involves transmitting or receiving an API key, typically comprising a lengthy sequence of alphanumeric characters. This key initiates programs from an external application; it identifies the code, its developer, the end-user, and the originating application of the API call.
Upon client authentication of the API key, the server validates their identity and grants access to the requested data.
As the proprietor of a network, it is not obligatory to divulge the intricate workings of website authentication to users. Instead, the focus should be on educating users about their API keys. Vital information such as authentication requests, error messages, handling of invalid authentication attempts, and the lifespan of tokens or codes should be provided to users.
It is imperative to instil a robust cybersecurity culture among users, emphasizing the importance of safeguarding their private keys, codes, or tokens and refraining from sharing them with unauthorized parties.
Common Methods of API Authentication
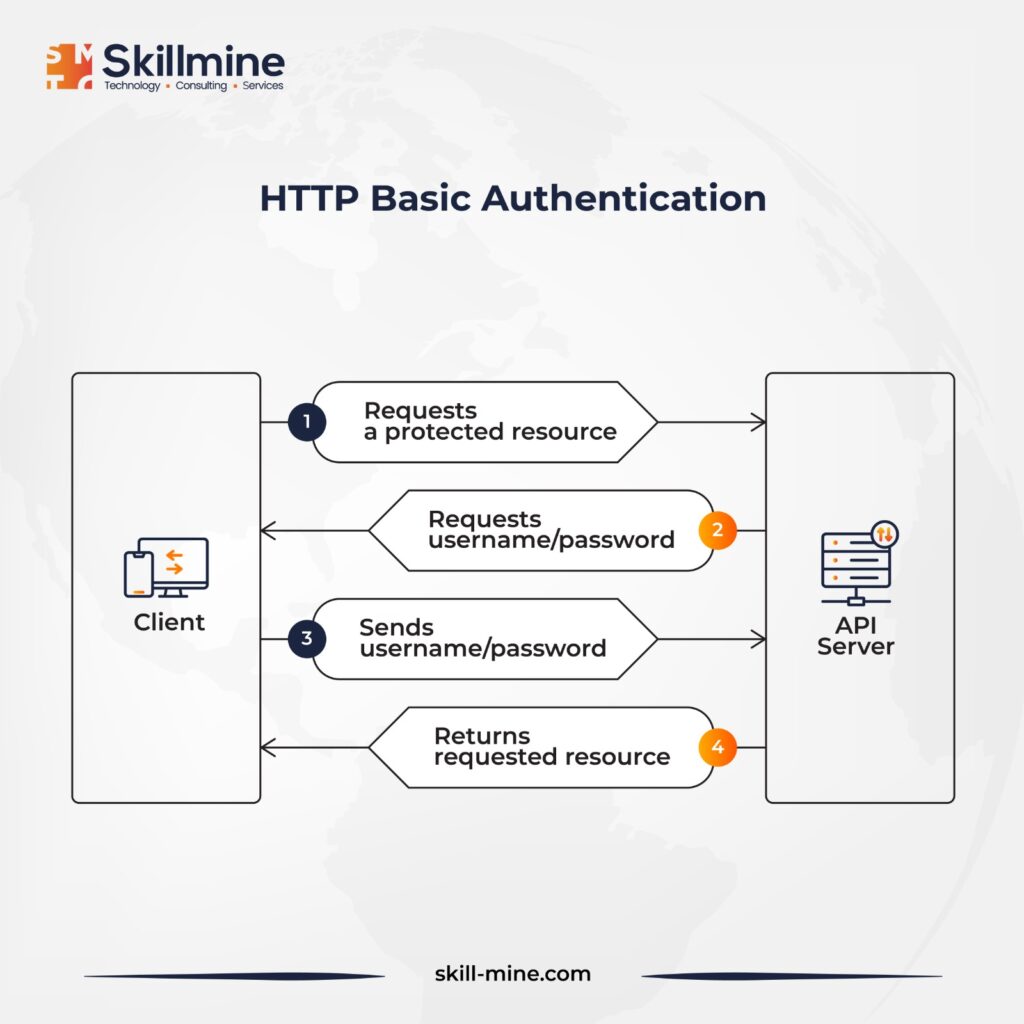
HTTP Basic Authentication: This represents the most fundamental approach to implementing API authentication. It entails transmitting credentials as user/password pairs within an Authorization header field, with the credentials encoded using Base64. However, this method lacks hashing or encryption, rendering it insecure unless utilized in tandem with HTTPS.
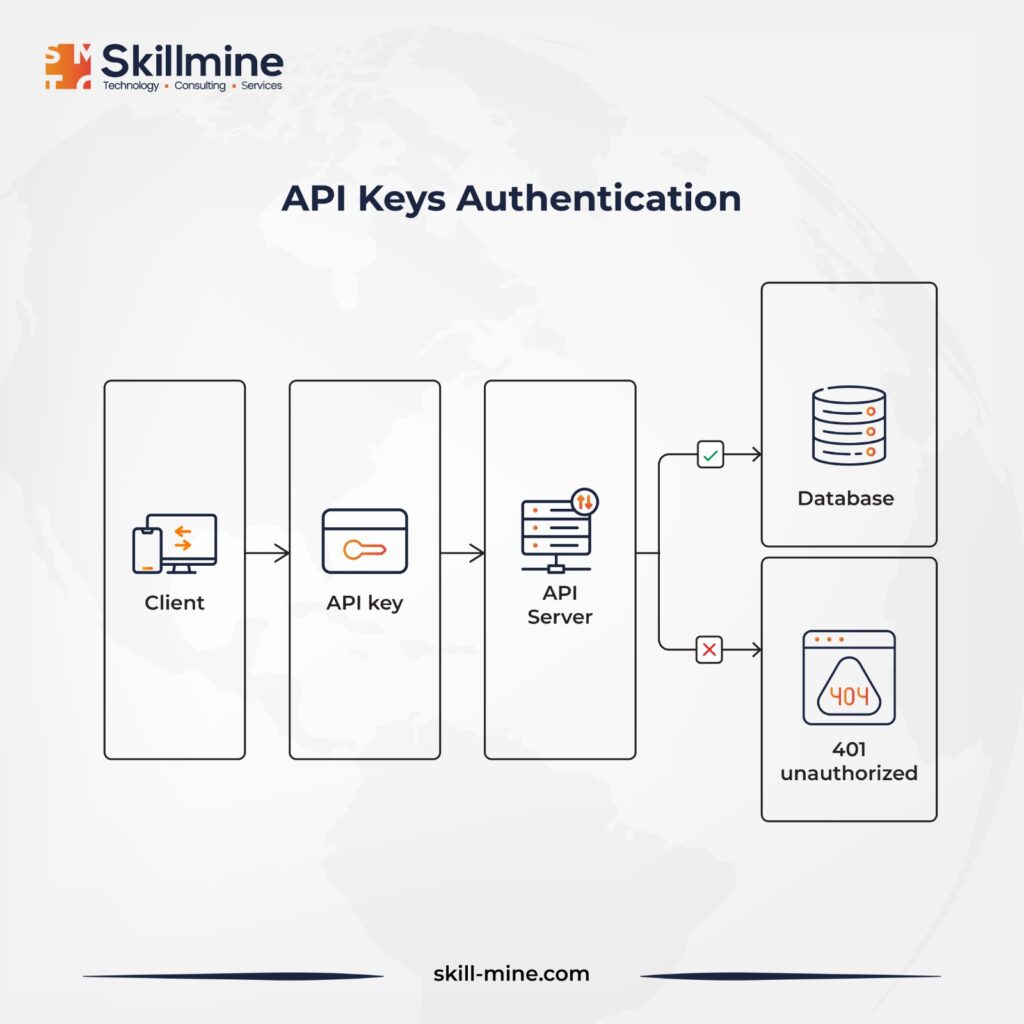
API Keys Authentication: In this authentication, unique identifiers are issued by API providers to registered users for controlling usage and monitoring access. These keys must accompany every request within the query string as a request header or cookie. Similar to HTTP basic authentication, API key authentication necessitates HTTPS to safeguard the key.
JWT (JSON Web Token): This method offers a compact, stateless means of API authentication. Upon a user’s login, the API server generates a digitally signed and encrypted JWT containing the user’s identity. Subsequently, the client includes the JWT in each subsequent request, which the server then deserializes and validates. This approach avoids storing user data on the server, enhancing scalability.
OAuth: This token-based authentication mechanism allows users to grant third-party access to their accounts without divulging login credentials. OAuth 2.0, offering enhanced flexibility and scalability over its predecessor OAuth 1.0, has become the standard for API authentication. It facilitates extensive API integration while safeguarding user data.





