Cybersecurity incidents and data breaches have unfortunately become all too common, resulting in substantial financial losses and damage to reputation. According to Statista, the global average cost of data breaches in the period from March 2022 to March 2023 was 4.45 million U.S. dollars. This figure underscores the urgent need for businesses to reinforce their security measures and proactively defend against potential threats. In this regard, Security Information and Event Management (SIEM) has emerged as an invaluable tool for organizations striving to protect their digital assets and sensitive data.
Understanding SIEM and its Benefits
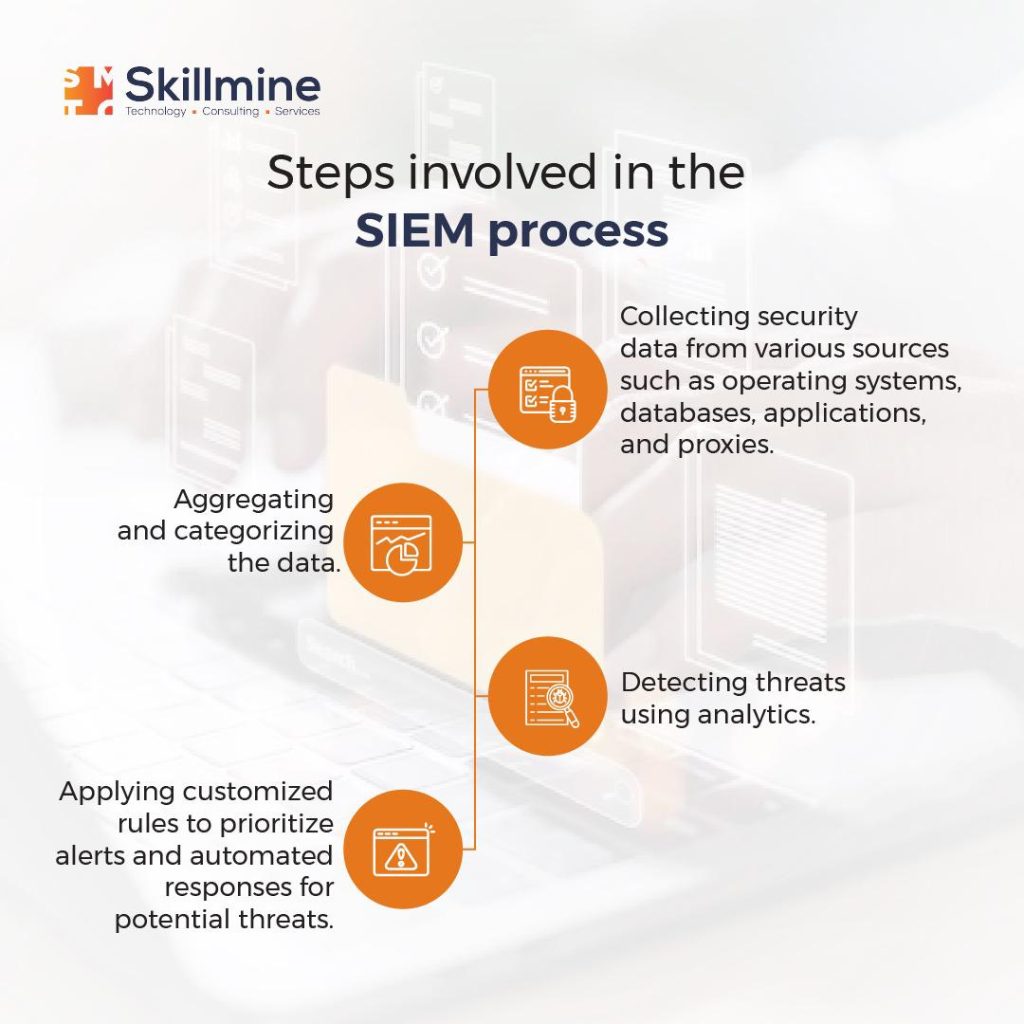
SIEM, known as Security Information and Event Management, offers a comprehensive approach to managing security incidents and threats. It involves collecting and analyzing data from various sources within an organization’s network infrastructure, such as logs, endpoints, and applications.
By adopting SIEM, businesses gain multiple significant advantages.
Benefit 1: Data Aggregation and Visibility
SIEM provides comprehensive visibility into your entire IT environment. It collects and stores data from various security tools in a centralized location, normalizing them into a uniform format for easy comparison and analysis. This allows you to make sense of vast amounts of data generated by different components in your IT infrastructure. By automating the process, SIEM saves you time and resources that would otherwise be spent manually analyzing data. It enables prompt detection of security incidents and helps you identify connections and patterns that might otherwise go unnoticed.
Benefit 2: Incident Detection
SIEM tools play a crucial role in incident detection, particularly for hosts that lack built-in detection capabilities. By correlating and analyzing log data from different systems, SIEM tools can detect incidents that might be missed by individual host logs. SIEM tools can reconstruct the series of events across multiple hosts, helping you understand the nature of an attack and its success. With timely alerts and access to associated log data, you can respond promptly to limit the damage caused by security threats.
Benefit 3: Improved Efficiency
SIEM tools significantly enhance your efficiency in understanding and handling security events. They provide a single interface to view security log data from different hosts, expediting the incident-handling process. This allows your IT team to quickly identify the route of an attack and the affected hosts. SIEM tools also include automated mechanisms to stop attacks in progress and contain compromised hosts, reducing the impact of a security breach. By working more efficiently and responding promptly to security incidents, you can minimize financial losses and mitigate damage.
Benefit 4: Simplified Compliance Reporting
Compliance with regulations is a critical aspect for businesses of all sizes and industries. SIEM tools simplify the compliance reporting process by collecting, normalizing, and organizing log data. With a centralized logging solution, you can easily generate rich, custom reports that include all the relevant security events from different hosts. This saves time and effort compared to manually retrieving data from each host and assembling individual reports. Accurate compliance reporting helps avoid hefty fines and loss of accreditation, ensuring your business meets regulatory requirements.
Understanding the Relationship between SOC and SIEM
SOC (Security Operations Center) and SIEM are interconnected concepts. SOC consists of highly skilled security analysts responsible for monitoring, analyzing, and responding to security incidents. To support SOC’s activities, SIEM serves as the technology backbone.
SOC analysts rely on SIEM tools to centralize and analyze vast amounts of security data, empowering them to proactively combat threats. The collaboration between SOC and SIEM ensures informed decision-making and prompt response to potential security incidents.
Conclusion
At Skillmine, we prioritize the paramount importance of security in today’s digital era. To ensure the highest levels of data protection for our clients, we employ robust security practices, including the implementation of SIEM. Leveraging SIEM technology allows us to monitor, detect, and respond to potential security incidents in real time, effectively safeguarding our clients’ valuable assets and maintaining the utmost level of data security at all times.
Looking for expert technology consulting services? Contact us today.










