CloudStrike’s 2024 Global Threat Report reveals a staggering 75% surge in cloud intrusions. With attackers operating stealthily and executing attacks within minutes, concealing their activities through valid credentials and legitimate tools, the challenges for cyber defenders have intensified. Incident response has emerged as a critical component in cybersecurity, underscoring the indispensable role of Security Operations Centers (SOC) service providers in incident handling. Let’s understand some best practices that can be employed in SOCs to optimize incident response effectiveness.
Build a Robust Foundation through Staffing and Training
Among the most critical strategies for incident response among SOC analysts is the establishment of a proficient team. This team should consist of adept professionals possessing expertise in various domains such as threat intelligence, malware analysis, forensics, and incident detection. To ensure clarity and consistency in approach, it’s essential to clearly define the roles and responsibilities of each team member. A standard staffing model may encompass Tier 1 and Tier 2 analysts, tools and support analysts, and intelligence threat analysts.
Craft a Comprehensive Incident Response Plan (IRP)
A well-rounded IRP should delineate the procedures, steps, and responsibilities inherent in the incident response process. The plan should also encompass a communication strategy and the assignment of roles and responsibilities during an incident. It should align with your organization’s priorities and its acceptable risk threshold. Conduct tabletop exercises and simulations with your team to pinpoint areas for improvement and to ensure preparedness for real incidents.
Create an Incident Response Playbook
Define various incident scenarios pertinent to your organization, outlining specific threat scenarios and response protocols. Subsequently, develop Standard Operating Procedures (SOPs) for each scenario, delineating precise steps and actions for SOC analysts. These SOPs serve as invaluable guides during incident response, facilitating swift and efficient action. Lastly, ensure continual updates to the playbook to align with emerging threats and evolving cybersecurity landscapes, thereby maintaining your team’s preparedness.
Adopt Incident Management Best Practices
Incorporating fault-free practices for cybersecurity incident management involves several key strategies. Firstly, adopt a multi-step incident response process, such as the NIST 4-step process or the SANS 6-phase process, which offer structured approaches ensuring adherence to best practices. Secondly, integrate Security Orchestration, Automation, and Response (SOAR) solutions to expedite incident response by automating routine tasks and providing tailored security playbooks.
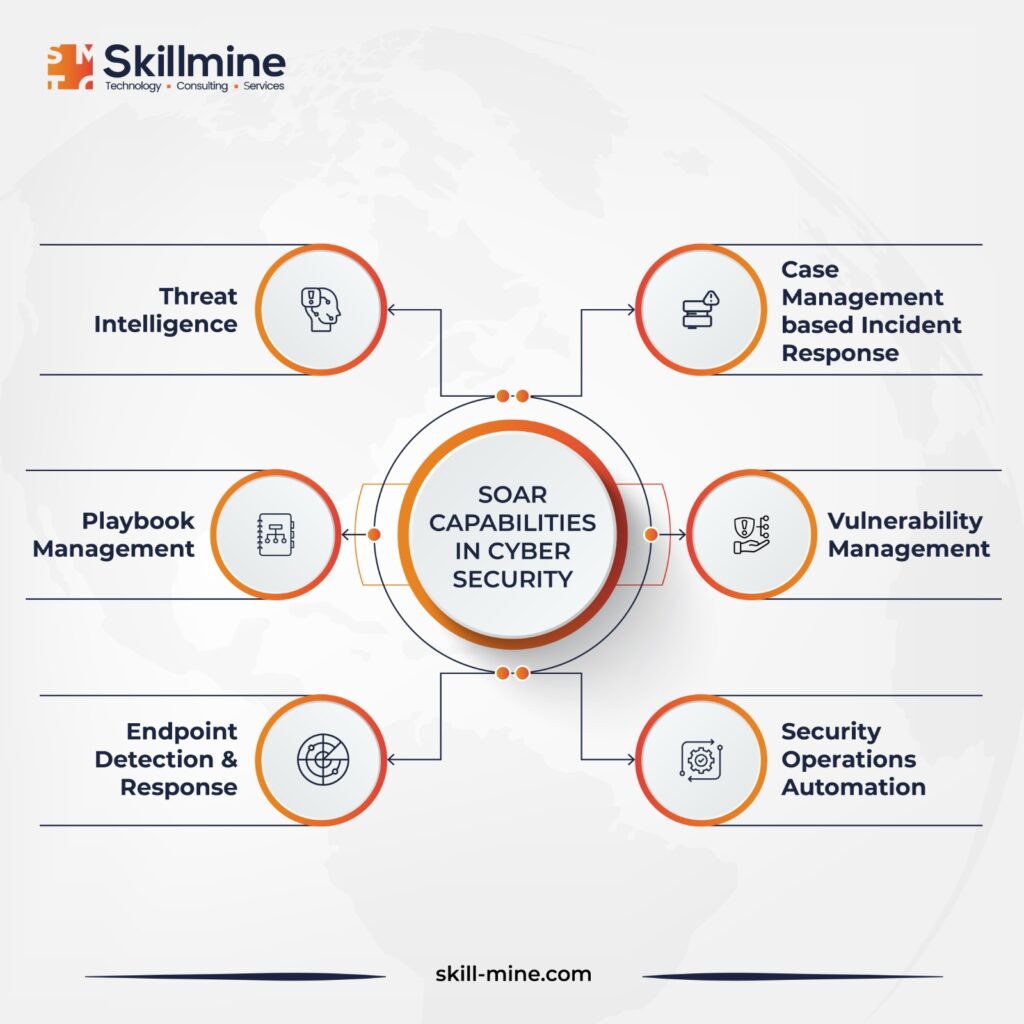
Additionally, prioritize post-incident analysis, conducting thorough assessments to glean insights, identify areas for enhancement, and continuously refine incident response capabilities.
Leverage the Latest Incident Response Tools
Integrate advanced threat detection solutions amalgamating both signature-based and signature-less controls, furnishing SOC analysts with extensive threat intelligence and visibility. Adopt centralized monitoring solutions, facilitating instant access to critical indicators of compromise, network telemetry, and logs from diverse infrastructure elements and security systems. Equip SOC analysts with forensic analysis tools enabling thorough incident investigations, characterized by ease of deployment, centralized data access, and rapid security incident evaluation, ensuring comprehensive response strategies.
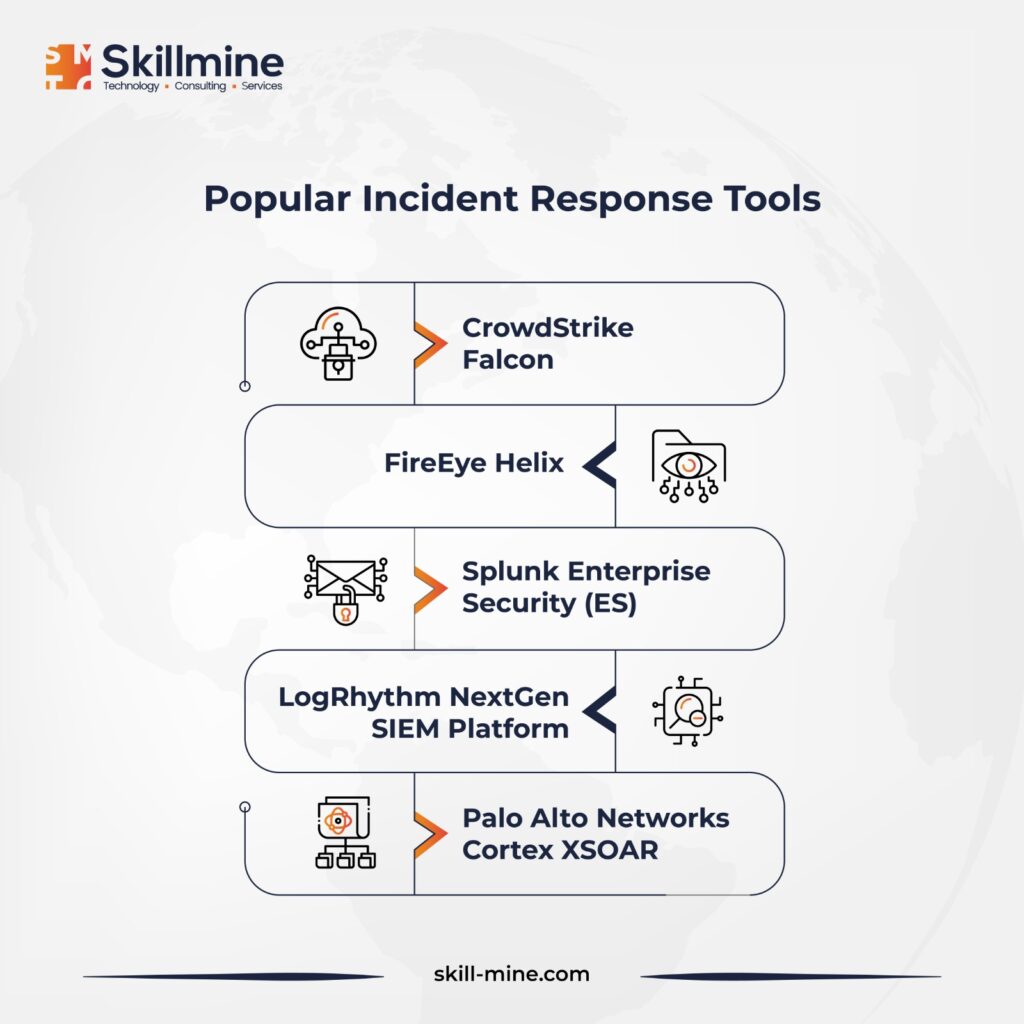

Enhance Incident Response Procedures
Standardize and streamline your incident response process across the organization to ensure consistency, minimize confusion, and expedite response times. Institute a culture of continuous improvement by regularly evaluating and refining incident response processes through the measurement of Key Performance Indicators (KPIs), conducting thorough post-mortem analyses, and integrating lessons learned into your Incident Response Plan (IRP). Foster collaboration with external partners such as law enforcement, industry peers, and cybersecurity experts to exchange threat intelligence and best practices.
Focus on Incident Containment and Recovery
Deploy swift containment strategies to curtail the impact of incidents and prevent further harm, including actions such as isolating affected systems, deactivating compromised accounts, and blocking malicious network traffic. Prioritize system restoration and recovery post-containment to minimize operational downtime and swiftly restore normal business operations.
Ensure Continuous Retesting and Training
Conduct regular security assessments to evaluate your organization’s security posture, pinpoint vulnerabilities, prioritize remediation efforts, and ensure the ongoing effectiveness of your incident response plan. Implement continuous training programs for SOC analysts and other staff members to keep them abreast of the latest threats, attack methodologies, and incident response protocols. Remember to test your organization’s incident response capabilities periodically by engaging in exercises such as penetration testing, red team/blue team simulations, and adversary emulation scenarios. These tests serve to identify areas for improvement and maintain preparedness for genuine incidents.
Conclusion
Effective incident response constitutes a pivotal aspect of a SOC’s responsibilities, and adhering to best practices is paramount for mitigating damage and minimizing downtime during security incidents. Preparation, proactive detection, containment, eradication, and recovery, coupled with proficient communication and thorough post-incident analysis, form the cornerstone of a successful incident response approach. By adopting these best practices, SOC service providers can bolster their organization’s capacity to promptly and efficiently address security incidents, thereby diminishing the impact of cyber threats. Skillmine’s SOC services provide businesses with comprehensive cybersecurity monitoring and incident response solutions, safeguarding their digital assets and mitigating the risk of cyberattacks.
Looking for expert technology consulting services? Contact us today.










