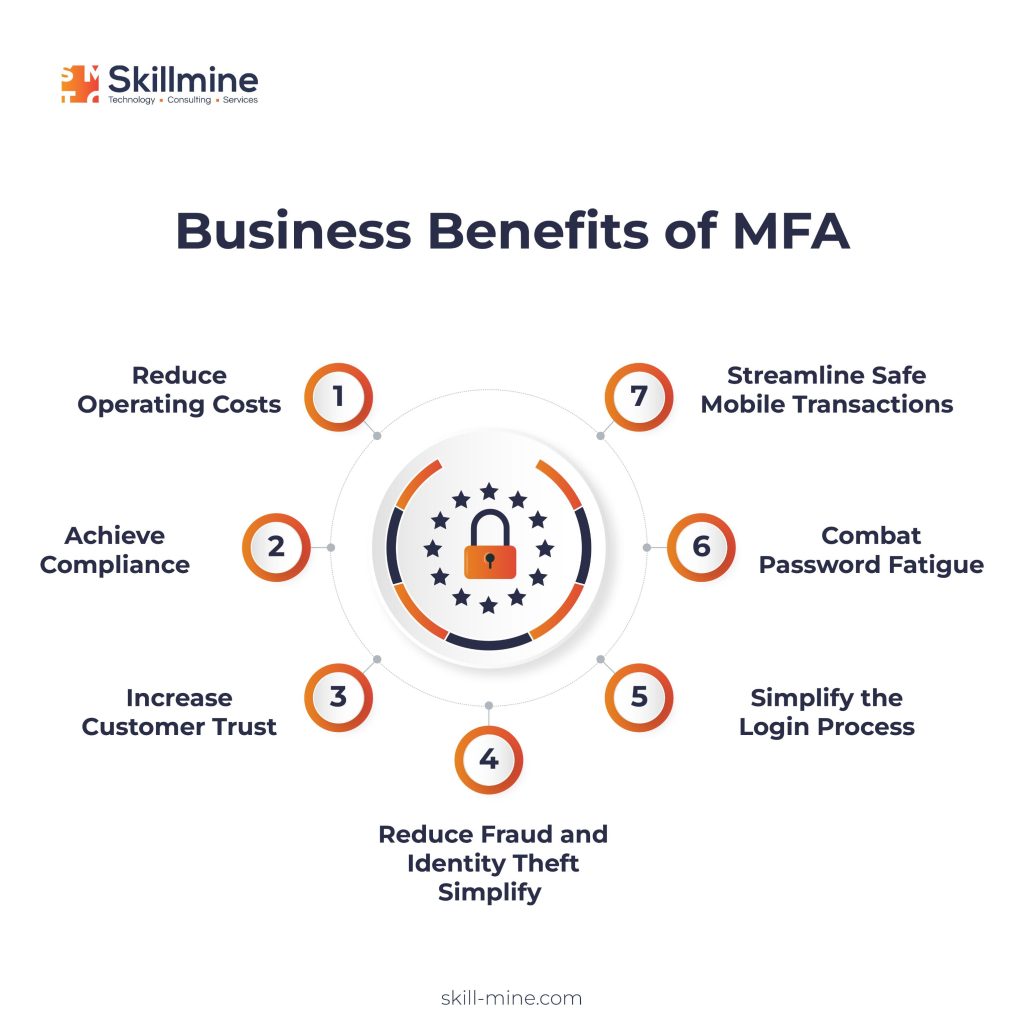
In today’s rapidly evolving digital landscape, securing your organization’s sensitive data and resources is of paramount importance. As cyber threats continue to grow in sophistication, traditional password-based authentication methods have proven to be inadequate in safeguarding against data breaches and unauthorized access. Multi-Factor Authentication (MFA) has emerged as a powerful solution to enhance security by adding an extra layer of protection beyond passwords. According to Microsoft, MFA can block over 99.9% of account compromise attacks, showcasing its efficacy in preventing unauthorized access.
Understanding the Significance of MFA
Multi-Factor Authentication (MFA) requires users to present two or more forms of identification to gain access to their accounts or systems. These factors can include something the user knows (password), something they have (a mobile device or smart card), and something they are (biometric data like fingerprints or facial recognition). The combination of these factors significantly reduces the risk of unauthorized access, even if passwords are compromised.
Let’s understand the essential factors to consider when choosing the right MFA solution for your organization.
Assess Your Organization’s Needs
Before choosing an MFA solution, it is crucial to evaluate your organization’s unique requirements. Consider factors such as the number of users, the devices and platforms being used, remote access needs, and compliance regulations applicable to your industry. Understanding these factors will help you identify the most suitable MFA solution for your organization.
User Experience and Convenience
While enhancing security is essential, an overly complex or burdensome MFA process can lead to user frustration and resistance. Opt for an MFA solution that strikes the right balance between security and user experience, offering streamlined and intuitive authentication methods. Mobile-based MFA solutions, like push notifications or one-time passcodes, are popular for their simplicity and convenience. A survey by IS Decisions revealed that 82% of users find MFA via a mobile app easier and more convenient than traditional methods.
Integration and Compatibility
Selecting an MFA solution that seamlessly integrates with your existing IT infrastructure is vital. Consider whether the solution is compatible with your applications, operating systems, and cloud services. An MFA solution that supports single sign-on (SSO) capabilities can further enhance user experience and reduce the administrative burden of managing multiple credentials.
Scalability and Future-Proofing
As your organization grows, your MFA needs may evolve. Choose an MFA solution that can scale with your organization and adapt to future technology advancements. A cloud-based MFA solution can be particularly advantageous, as it allows for easy scalability and continuous updates without significant hardware investments.
Security and Compliance
The 2020 Verizon Data Breach Investigations Report highlighted that 81% of hacking-related breaches leveraged stolen or weak passwords, emphasizing the need for robust authentication methods like MFA. When evaluating MFA solutions, prioritize security features like encryption, secure protocols, and strong authentication methods. Additionally, ensure that the MFA solution complies with industry regulations and data protection standards applicable to your organization. Regulatory bodies such as GDPR, HIPAA, and PCI-DSS may have specific requirements for authentication practices.
Reporting and Monitoring Capabilities
Comprehensive reporting and monitoring functionalities are crucial for understanding user behaviour and identifying potential security threats. Look for an MFA solution that provides detailed logs and real-time alerts to help your IT team detect and respond to suspicious activities promptly.
Conclusion
Selecting the right MFA solution is a critical step in safeguarding your organization’s digital assets and sensitive data. Embracing the power of MFA will not only fortify your organization’s security posture but also instil confidence in your stakeholders that their data is in safe hands. Skillmine’s Authenticator stands out as an exemplary MFA solution that combines robust security with user-friendly features. By using MFA and SSO, Skillmine’s Authenticator centralizes access management while offering top-notch protection against cyber threats.
Looking for expert technology consulting services? Contact us today.





