As enterprises migrate to the cloud for speed, agility, and scalability, a quieter risk often gets overlooked: cloud misconfigurations. These minor oversights are now the leading cause of cloud data breaches, silently draining security budgets and exposing organizations to preventable risks.
Misconfigurations: Small Errors, Massive Consequences
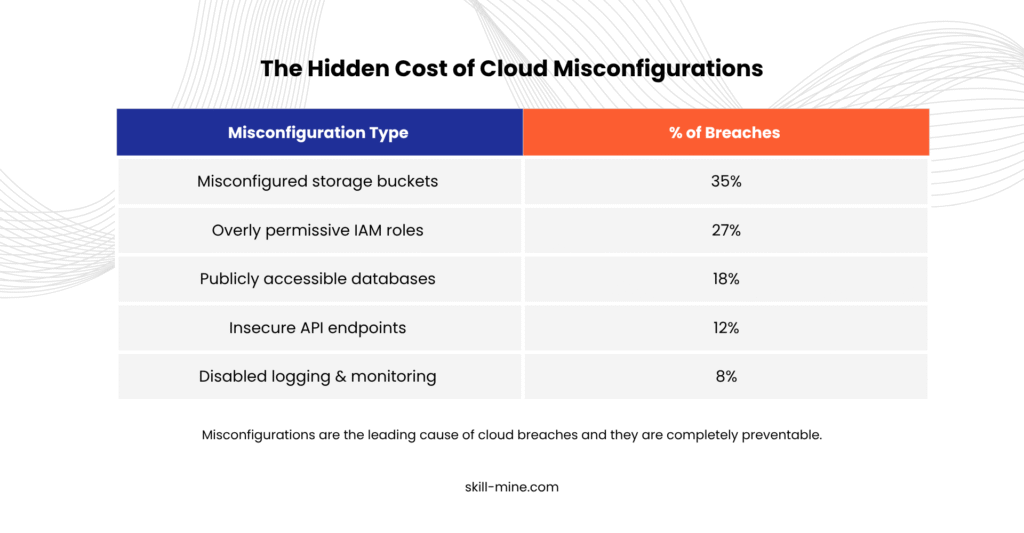
Cloud misconfigurations happen when system settings are insecure, incomplete, or incorrect, leading to vulnerable services, direct access, and compliance failures. These are not rare anomalies; they are a persistent issue across industries and sectors.
Few Examples:
Few Examples:
- Capital One (2019): A misconfigured AWS security system allowed a hacker to access 100M+ customer accounts, leading to $80M in penalties. → Source: TechCrunch.
- Facebook (2019): A third-party app left a public cloud database exposed, affecting over 540M user records. → Source: ZDNet.
- Accenture (2021): Misconfigured cloud storage buckets led to the exposure of 6TB of internal data. → Source: CyberNews.
Why Misconfigurations Happen Frequently?
Despite having skilled teams and mature tooling, misconfigurations persist due to:
- Cloud Complexity: Multi-cloud environments and rapid deployments cause inconsistent configuration management.
- Speed Over Security: DevOps prioritises fast delivery, often at the cost of proper security configurations.
- Manual Processes: Manual reviews and audits are time-consuming and error prone.
- Lack of Visibility: Organizations struggle to monitor thousands of assets in real time.
- Shadow IT: Teams launch cloud services independently, bypassing IT policies and security checks.
The Financial Fallout.
Cloud misconfigurations are not just security risks; they are budget killers.
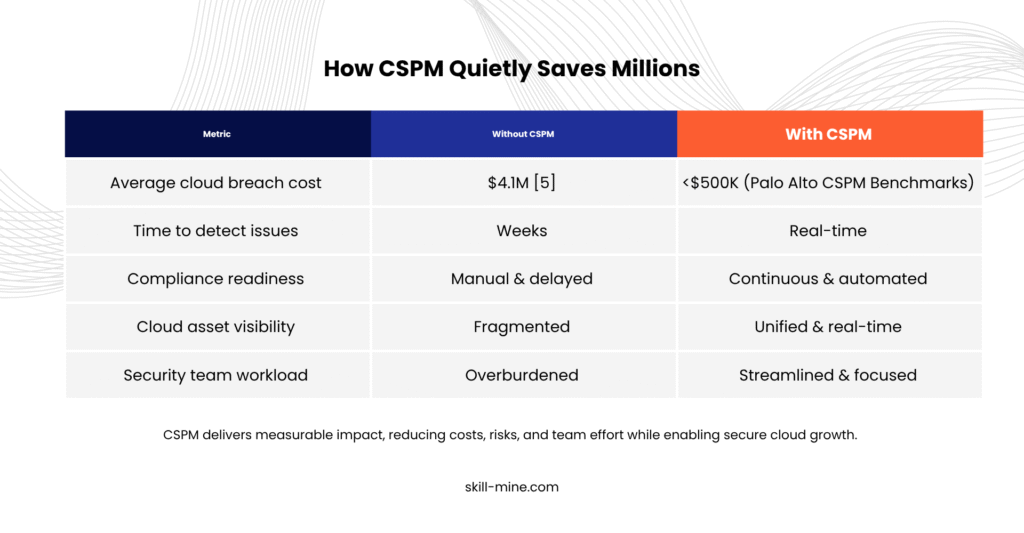
- The average cost of a cloud-related breach in 2024 is $4.1 million. → Source: IBM Cost of a Data Breach Report 2024.
- Regulatory penalties for violating GDPR, HIPAA, or PCI-DSS can reach millions of dollars, depending on the severity and industry. → Source: European Commission GDPR Guidelines
CSPM: Your First Line of Defense Against Cloud Chaos
Cloud Security Posture Management (CSPM) is a preventive and continuous approach to combat misconfigurations. It is not a security system. CSPM tools analyze configurations, enforce security policies, and automate fixes.
What CSPM offers:
- Asset Discovery: Identifies every resource across AWS, Azure, GCP, and hybrid environments.
- Security Monitoring: Flags security risks in IAM policies, public IPs, security system rules, and more.
- Compliance Auditing: Ensures continuous adherence to industry standards like CIS, NIST, and PCI-DSS.
- Risk Prioritization: Highlights high-impact issues, like exposed credentials or databases.
- Remediation: Supports auto-remediation or ticket-based workflows.
- Reporting: Dashboards and audit-ready compliance reports for stakeholders.
Why CSPM Works Silently but Powerfully?
CSPM tools operate behind the scenes, continuously:
- Auditing every cloud service
- Detecting misconfiguration in real-time
- Reducing manual workload
- Avoiding last-minute compliance sprints
- Preventing incidents before they happen
Security That Pays for Itself.
Cloud misconfigurations will not resolve themselves. But with tools like CSPM, organizations can address the root of most cloud security issues.
- Instead of reacting to breaches, proactively prevent them from happening.
- Instead of pouring money into incident response, invest in posture management.
- Instead of searching for errors manually, automate visibility and remediation.
Ready to Strengthen Your Cloud Posture?
At Skillmine, we specialize in helping enterprises:
- Assess cloud misconfigurations.
- Deploy CSPM across multi-cloud setups.
- Maintain continuous compliance and visibility.
Let us secure your cloud quietly, continuously, and cost-effectively.





