“Zero trust” is a cybersecurity strategy where the application of security policy is based on the context created through least-privileged access controls and rigorous user authentication- as opposed to presumed trust. A well-tuned zero trust architecture can improve user experience, network infrastructure, and cyber threat defence.
Understanding Zero Trust Architecture
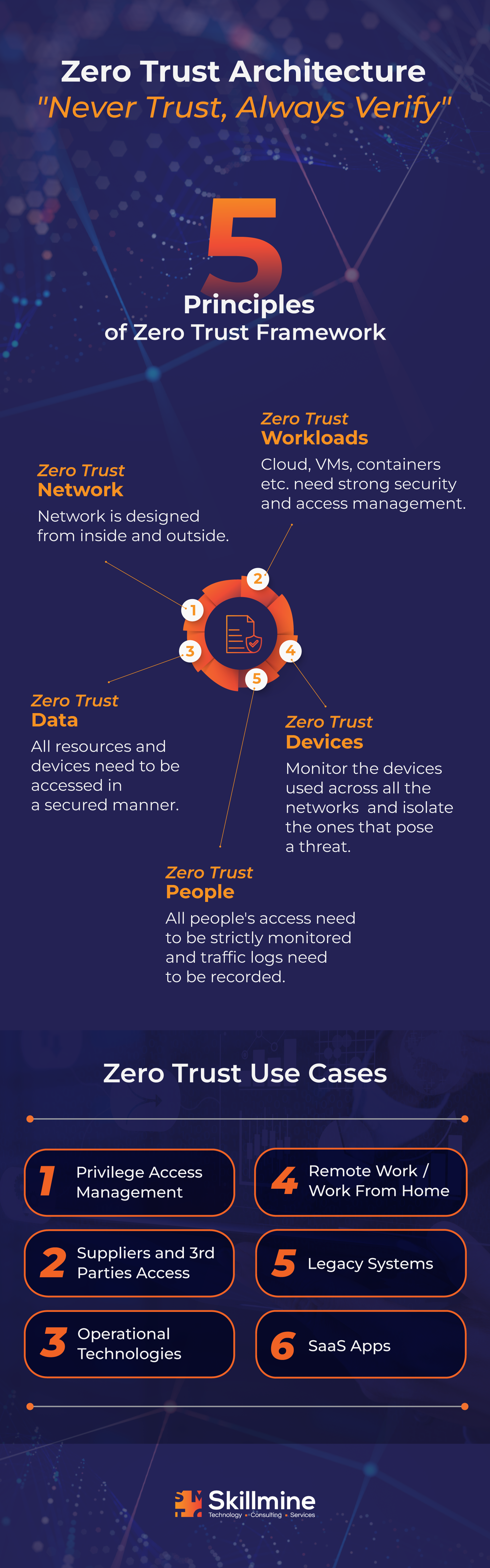
‘Zero Trust Architecture’ is a term coined by John Kindervag, a former analyst at Forrester. It follows the maxim “never trust, always verify”. To prevent unauthorised access and lateral movement around an environment, a zero-trust architecture enforces access regulations based on context, including the user’s role and location, device, and the data they request.
Establishing a zero trust architecture calls for strong multifactor authentication (MFA) methods beyond passwords, such as biometrics or one-time codes. It also requires visibility and control over the environment’s users and traffic, including encrypted traffic and monitoring and verifying traffic between parts of the domain.
With a zero trust architecture, a resource’s location on the network is no longer the primary determinant of its security posture. Your data, workflows, services, and other items are protected by software-defined micro-segmentation rather than complex network segmentation. This lets you keep them secure anywhere in your data centre or dispersed hybrid and multi-cloud settings.
How does zero trust architecture work?
Zero trust’s fundamental tenet is to assume everything is hostile by default. It represents a significant divergence from the 1990s-era network security concept based on a centralised data centre and a protected network perimeter. To set access controls and validate what is trusted inside the network, including often anyone accessing via remote access VPN, these network architectures rely on approved IP addresses, ports, and protocols.
In contrast, a zero trust strategy views all traffic as hostile, regardless of whether it is currently inside the perimeter. Identity-based validation policies provide more robust security. It follows the workload wherever it communicates, whether in a public cloud, a hybrid environment, a container, or an on-premises network architecture.
Zero trust safeguards applications and services even when they communicate across network environments, requiring no architectural changes or policy updates because protection is environment-agnostic. Zero trust uses corporate policies to safely connect users, devices, and applications over any network. This enables digital transformation.
Benefits of zero trust architecture
Zero trust is one of the most effective security measures available today, despite the fact that no security measure is flawless, and data breaches can never be entirely eradicated. Zero trust reduces the attack surface and the severity of cyberattacks, reducing the time and money needed to respond to breaches and clean them up.
Not to mention that the best method for cloud security currently available is a zero-trust security paradigm. Given the cloud, endpoint, and data sprawl in today’s IT settings, the capacity to not trust any connection without adequate verification is crucial.
Conclusion:
According to The US National Institute of Standards and Technology (NIST) Special Publication NIST SP 800-207, “Most enterprises will continue to operate in a hybrid zero-trust/perimeter-based mode for a period while continuing to invest in ongoing IT modernization initiatives”. Zero trust architecture is neither a singular off-the-shelf product nor a service. Migration to a zero trust architecture may not happen in a single technology refresh cycle. Instead, it should be seen as a journey.
Looking for expert technology consulting services? Contact us today.