‘Congratulations! You have won $100000!’
‘You have just won a free vacation package to Greece!’
Ever came across emails that begin this way? These are examples of bait attack, a clever manipulation tactic used by cybercriminals to trick unsuspecting victims into compromising their security. Here, cybercriminals exploit human curiosity, greed, or the desire for personal gain. Bait attacks typically involve the use of enticing ‘baits’ such as fake websites, enticing offers or infected USB drives.
The objective of a bait attack is to exploit unsuspecting individuals into taking actions that compromise their security. Cybercriminals often utilize enticing offers, false promises, or deceptive content to manipulate their victims into taking harmful actions like,
- Clicking on malicious links,
- Downloading files containing malware,
- Divulging sensitive information such as passwords or financial details.
Common bait attacks
Online shopping scams
Attackers create fake online stores that mimic legitimate e-commerce websites. They offer attractive discounts or exclusive deals on popular products to lure unsuspecting shoppers. Once users make a purchase, their credit card information is stolen, leading to financial loss and potential identity theft.
Social Media Contests
Cybercriminals create fraudulent social media accounts or pages that appear to belong to reputable companies or organizations. They announce fake contests or giveaways, asking participants to provide personal information, share posts, or click on malicious links to enter. These scams are designed to collect sensitive data or spread malware.
Phishing Emails
Phishing emails are a common form of bait attack. Attackers impersonate well-known companies or organizations and send emails asking recipients to update their account details or verify sensitive information. These emails often contain links that lead to fake websites where victims unknowingly enter their credentials, which are then captured by the attackers.
Fake Software Updates
Attackers take advantage of software vulnerabilities by distributing fake software update notifications. These notifications often mimic legitimate updates from well-known software providers. When users click on the update links, malware is installed on their systems, allowing attackers to gain unauthorized access or control over their devices.
Job Offer Scams
Cybercriminals post fake job offers on online job portals, targeting job seekers. These scams promise lucrative positions or work-from-home opportunities and request personal information or upfront payments for processing fees. Victims may end up providing sensitive data or losing money to fraudsters.
To safeguard against bait attacks, the following preventive measures can be employed:
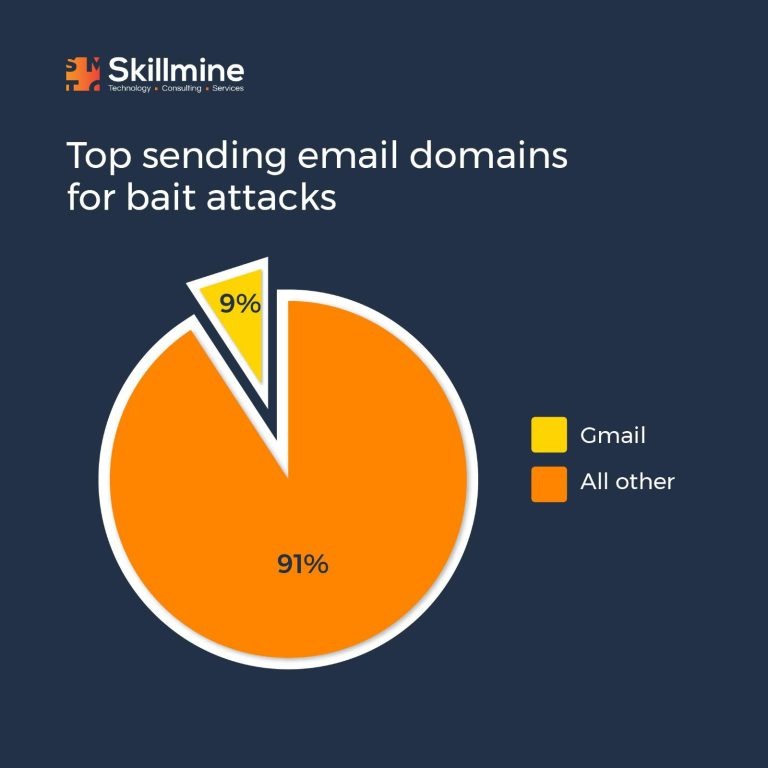
Deploy AI-based defence: Traditional filtering technologies often struggle to detect and block bait attacks effectively. As these attacks do not carry any malicious payload and are typically sent from reputable platforms like Gmail, AI-based defence systems prove to be more efficient. Leveraging data from multiple sources, including communication graphs, reputation systems, and network-level analysis, AI-powered solutions provide better protection against such attacks.
Train users to recognize and report bait attacks: While some bait attacks may still make their way into users’ inboxes, it is crucial to educate employees on how to identify and avoid falling victim to these attacks. Incorporate examples of bait attacks in security awareness training and simulation campaigns. Encourage users to report any suspicious emails to the IT and security teams promptly.
Promptly remove bait attacks from inboxes: Once identified, it is vital to swiftly remove bait attacks from users’ inboxes to prevent them from opening or responding to the messages. Automated incident response systems can assist in identifying and remedying these messages within minutes, curbing the spread of the attack and reducing the chances of the organization becoming a future target.
Conclusion
Bait attacks pose a significant challenge to traditional phishing detection methods. Attackers exploit human curiosity and employ subtle tactics to bypass security measures. Organizations can bolster their defences against bait attacks and minimize the potential risks associated with them by taking necessary precautions. The Skillmine team has prepared a checklist you can follow to ensure that your business fulfils all the cybersecurity parameters: The Key Cybersecurity Requirements Every Business Should Meet
Looking for expert technology consulting services? Contact us today.










