A Network Operations Center, or NOC, is a centralized place where network operations employees supervise, monitor, and administer the network, servers, databases, firewalls, devices, and related external services throughout the year. This infrastructure environment could be on-premises or hosted by a cloud provider.
As a result of technological advancements, network traffic flows have altered, and application support has become more challenging. Due to this, network operations need to be more proactive and implement comprehensive visibility tools for their environments. Global market intelligence solutions provider International Data Corporation (IDC) has the same view. It says that proactive network operations are the need of the hour. Network teams should transition from tactical activities, in which they only deploy, fix, and maintain operations, to strategic tasks that enable innovation and automation.
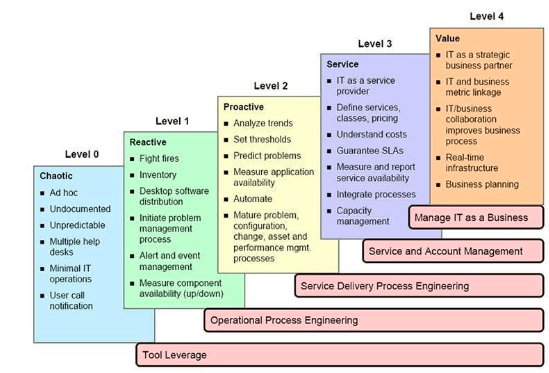
Take a look at this graphic (Source: Gartner) that shows how eager many IT service providers are to transition from providing services to providing value. The only way to do that is by automation. This explains the importance of NOC automation ( NOC Tools ).
These days, NOC teams are prioritizing modernization in the following areas:
- Network security.
- Network virtualization.
- Optimization of network operations.
Here are some key factors to consider when automating NOC.
The Shift From Being Reactive to Being Proactive
The NOC needs processes that automate how the network detects and resolves service-impacting events in real time. Reacting to bad situations or client complaints is time-consuming and expensive. Automation and Machine Learning can improve the business’ capacity to anticipate and stop problems before they happen.
Data Should be Added to a Single Platform.
Any network operations team’s ability to quickly gather and process information is essential to its success. Communication Service Providers (CSPs), Managed Service Providers (MSPs), and other businesses have struggled in the past to quickly and accurately visualise their expanding networks in a single view, relying instead on legacy tools and manual procedures to keep an eye on vital network functions and services. The proliferation of inventory systems, segregated applications, and fractured network infrastructures combined through mergers creates a significant visibility gap in the NOC. Unifying data under a single platform can simplify access to information.
Root-cause analysis
Once the data is consolidated data in a single platform, analyze and resolve the root cause of service-impacting events. Eliminate gaps to ensure your operations team always acts correctly against incidents resulting in impacted services.
Using Machine Learning and Data Analytics to produce a single root cause event, you can identify anomalies, such as temporal deviations and statistical rarities. Root causal events contain suppression patterns that filter out noise to improve NOC operators’ rate of predictability to resolve problems versus responding to a storm of event alarms (again, allowing you to be proactive instead of reactive).
Benefits of NOC Automation
Automating Network Operations Center (NOC) tasks yields numerous advantages. It enhances efficiency by automating routine tasks, thereby reducing the likelihood of human error. Additionally, it bolsters network visibility, empowering NOC teams to swiftly detect and address network issues.
Moreover, automating NOC services fortifies security by facilitating real-time monitoring of network activities and automatic responses to security threats. It also enables high automation and improved configuration management, ensuring correct and consistent configuration of network devices.
Challenges in Implementing NOC Automation
Despite its benefits, implementing NOC automation can pose challenges. Compatibility and integration issues stand out as primary hurdles. Not all network devices support the same communication protocols, complicating their integration into an automated system.
Security emerges as another concern. While automation can enhance network security, improper implementation may introduce new vulnerabilities. Hence, it’s imperative to prioritize security when planning for NOC automation.
Staff training constitutes a crucial aspect. NOC engineers require training on developing and utilizing new automation tools, as well as managing automated systems.
Best Practices for Implementing NOC Automation
To surmount these challenges, adhering to best practices is essential when introducing automated NOC tools and services. These practices include:
- Planning: Thoroughly understand network operations and identify tasks suitable for automation before implementation.
- Tool Selection: Choose NOC automation tools that align with your requirements and are compatible with network devices.
- Training: Ensure NOC personnel receive comprehensive training on utilizing automation tools and managing automated systems.
- Security: Integrate security considerations at every stage of implementation, from selecting secure automation tools to regular monitoring for security issues.
- Continuous Improvement: View NOC automation as an ongoing process rather than a one-time project. Regularly assess system performance and implement enhancements as needed.
Conclusion
Understanding where to employ automation and Machine Learning technologies inside the many processes that a NOC supports is essential for their effective utilisation. NOC automation becomes successful only when there is a strong foundation in NOC best practices and a well-developed organizational structure. This includes good knowledge management and training practices. Know how Skillmine’s NOC services have been helping businesses with improved network monitoring, incident response and threat analysis
Looking for expert technology consulting services? Contact us today.